PT0-001 Online Practice Questions and Answers
In a physical penetration testing scenario, the penetration tester obtains physical access to a laptop following potential NEXT step to extract credentials from the device?
A. Brute force the user's password.
B. Perform an ARP spoofing attack.
C. Leverage the BeEF framework to capture credentials.
D. Conduct LLMNR/NETBIOS-ns poisoning.
While reviewing logs, a web developer notices the following user input string in a field:
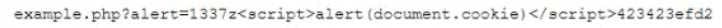
Which of the following types of attacks was done to the website?
A. XSS injection
B. Blind XSS
C. Reflected XSS
D. Persistent XSS
Which of the following documents BEST describes the manner in which a security assessment will be conducted?
A. BIA
B. SOW
C. SLA
D. MSA
Which of the following actions BEST matches a script kiddie's threat actor?
A. Exfiltrate network diagrams to perform lateral movement
B. Steal credit cards from the database and sell them in the deep web
C. Install a rootkit to maintain access to the corporate network
D. Deface the website of a company in search of retribution
A penetration tester has been assigned to perform an external penetration assessment of a company. Which of the following steps would BEST help with the passive-information-gathering process? (Choose two.)
A. Wait outside of the company's building and attempt to tailgate behind an employee.
B. Perform a vulnerability scan against the company's external netblock, identify exploitable vulnerabilities, and attempt to gain access.
C. Use domain and IP registry websites to identify the company's external netblocks and external facing applications.
D. Search social media for information technology employees who post information about the technologies they work with.
E. Identify the company's external facing webmail application, enumerate user accounts and attempt password guessing to gain access.
After establishing a shell on a target system, Joe, a penetration tester is aware that his actions have not been detected. He now wants to maintain persistent access to the machine. Which of the following methods would be MOST easily detected?
A. Run a zero-day exploit.
B. Create a new domain user with a known password.
C. Modify a known boot time service to instantiate a call back.
D. Obtain cleartext credentials of the compromised user.
A penetration tester is performing a black-box test of a client web application, and the scan host is unable to access it. The client has sent screenshots showing the system is functioning correctly. Which of the following is MOST likely the issue?
A. The penetration tester was not provided with a WSDL file.
B. The penetration tester needs an OAuth bearer token.
C. The tester has provided an incorrect password for the application.
D. An IPS/WAF whitelist is in place to protect the environment.
A penetration tester has SSH access to a Linux server that is exposed to the internet and has access to a corporate internal network. This server, with IP address 200.111.111.9, only has port TCP 22 externally opened. The penetration tester also discovered the internal IP address 192.168.1.5 from a Windows server. Which of the following steps should the penetration tester follow to open an RDP connection to this Windows server and to try to log on?
A. Connect to the Linux server using # ssh 200.111.111.9, establish an RDP connection to the 192.168.1.5 address.
B. Connect to the Windows server using # ssh -L 3389:200.111.111.9:22 192.168.1.5.
C. Connect to the Linux server using # ssh -L 3389:192.168.1.5:3389 200 .111.111.9; RDP to localhost address, port 3389.
D. Connect to the Windows server using # ssh -L 22:200.111.111.9:3389 192.168.1.5.
A client gives a penetration tester a /8 network range to scan during a week-long engagement. Which of the following tools would BEST complete this task quickly?
A. Massscan
B. Nmap
C. Angry IP scanner
D. Unicorn scan
During a penetration test, a host is discovered that appears to have been previously compromised and has an active outbound connection. After verifying the network activity is malicious, which of the following should the tester do?
A. Inform the client to shut it down and investigate.
B. Take action and shut it down immediately.
C. Inform the client and allow them to respond.
D. Note the finding and continue the assessment.

