PCCSE Online Practice Questions and Answers
A security team has a requirement to ensure the environment is scanned for vulnerabilities. What are three options for configuring vulnerability policies? (Choose three.)
A. individual actions based on package type
B. output verbosity for blocked requests
C. apply policy only when vendor fix is available
D. individual grace periods for each severity level
E. customize message on blocked requests
Per security requirements, an administrator needs to provide a list of people who are receiving e-mails for Prisma Cloud alerts. Where can the administrator locate this list of e-mail recipients?
A. Target section within an Alert Rule.
B. Notification Template section within Alerts.
C. Users section within Settings.
D. Set Alert Notification section within an Alert Rule.
An administrator needs to detect and alert on any activities performed by a root account. Which policy type should be used?
A. config-run
B. config-build
C. network
D. audit event
Given the following audit event activity snippet:
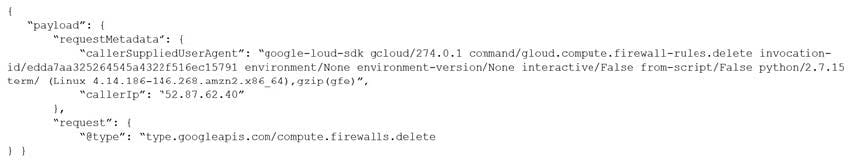
Which RQL will be triggered by the audit event?
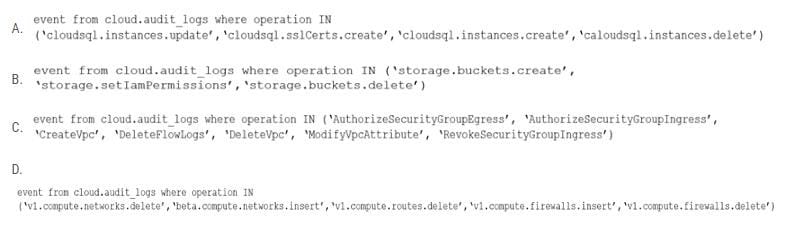
A. Option A
B. Option B
C. Option C
D. Option D
Who can access saved searches in a cloud account?
A. Administrators
B. Users who can access the tenant
C. Creators
D. All users with whom the saved search has been shared
When configuring SSO how many IdP providers can be enabled for all the cloud accounts monitored by Prisma Cloud?
A. 2
B. 4
C. 1
D. 3
What are two built-in RBAC permission groups for Prisma Cloud? (Choose two.)
A. Group Membership Admin
B. Group Admin
C. Account Group Admin
D. Account Group Read Only
What are the three states of the Container Runtime Model? (Choose three.)
A. Initiating
B. Learning
C. Active
D. Running
E. Archived
Taking which action will automatically enable all seventy levels?
A. Navigate to Policies > Settings and enable all severity levels in the alarm center.
B. Navigate to Settings > Enterprise Settings and enable all severity levels in the alarm center.
C. Navigate to Policies > Settings and ensure all severity levels are checked under "auto-enable default policies."
D. Navigate to Settings > Enterprise Settings and ensure all severity levels are checked under "auto-enable default policies."
Which RQL query will help create a custom identity and access management (IAM) policy to alert on Lambda functions that have permission to terminate EC2 instances?
A. iam from cloud.resource where dest.cloud.type = ’AWS

