NSE8_812 Online Practice Questions and Answers
Refer to the exhibit.
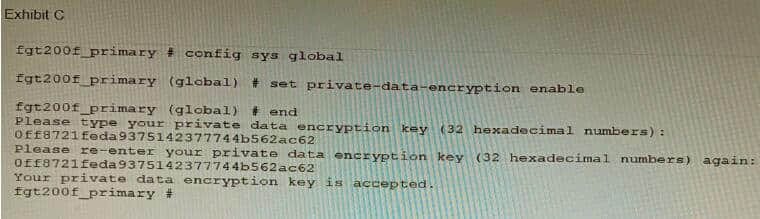
A customer has deployed a FortiGate 200F high-availability (HA) cluster that contains and TPM chip. The exhibit shows output from the FortiGate CLI session where the administrator enabled TPM.
Following these actions, the administrator immediately notices that both FortiGate high availability (HA) status and FortiManager status for the FortiGate are negatively impacted.
What are the two reasons for this behavior? (Choose two.)
A. The private-data-encryption key entered on the primary did not match the value that the TPM expected.
B. Configuration for TPM is not synchronized between FortiGate HA cluster members.
C. The FortiGate has not finished the auto-update process to synchronize the new configuration to FortiManager yet.
D. TPM functionality is not yet compatible with FortiGate HA D The administrator needs to manually enter the hex private data encryption key in FortiManager
You must analyze an event that happened at 20:37 UTC. One log relevant to the event is extracted from FortiGate logs:

The devices and the administrator are all located in different time zones Daylight savings time (DST) is disabled The FortiGate is at GMT-1000. The FortiAnalyzer is at GMT-0800 Your browser local time zone is at GMT-03.00
You want to review this log on FortiAnalyzer GUI, what time should you use as a filter?
A. 20:37:08
B. 10:37:08
C. 17:37:08
D. 12.37:08
You must configure an environment with dual-homed servers connected to a pair of FortiSwitch units using an MCLAG.
Multicast traffic is expected in this environment, and you should ensure unnecessary traffic is pruned from links that do not have a multicast listener.
In which two ways must you configure the igmps-f lood-traffic and igmps-flood-report settings? (Choose two.)
A. disable on ICL trunks
B. enable on ICL trunks
C. disable on the ISL and FortiLink trunks
D. enable on the ISL and FortiLink trunks
Refer to the exhibit showing the history logs from a FortiMail device.
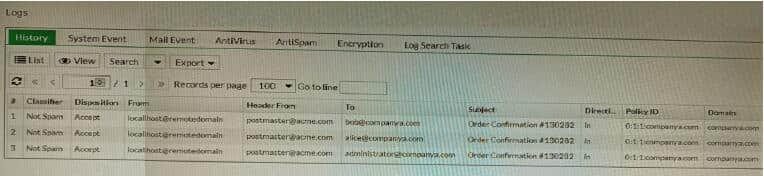
Which FortiMail email security feature can an administrator enable to treat these emails as spam?
A. DKIM validation in a session profile
B. Sender domain validation in a session profile
C. Impersonation analysis in an antispam profile
D. Soft fail SPF validation in an antispam profile
Refer to the exhibits.
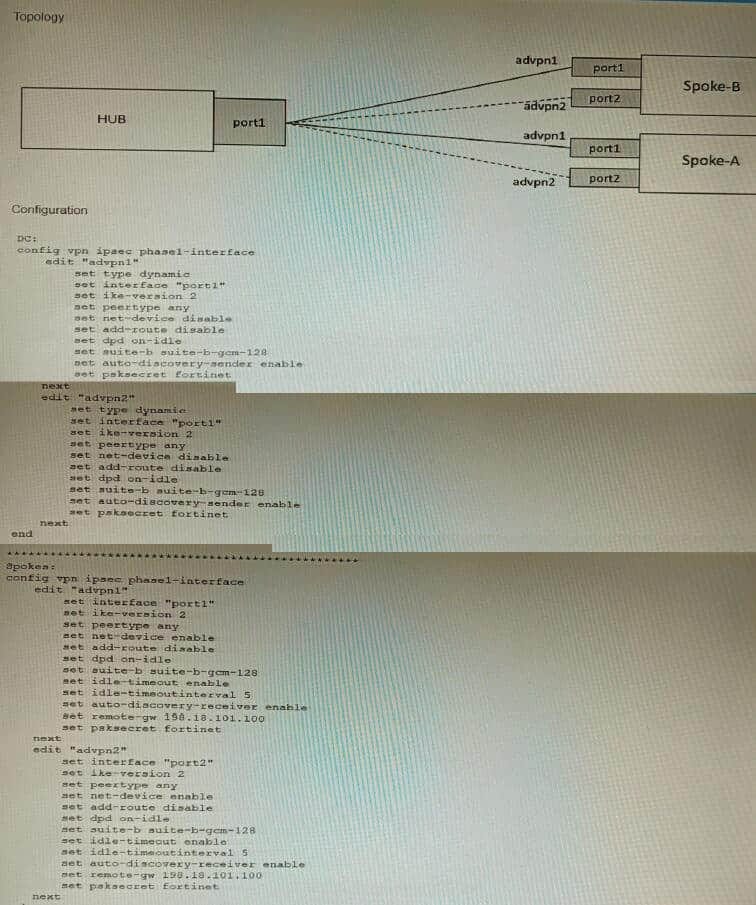
The exhibits show a diagram of a requested topology and the base IPsec configuration.
A customer asks you to configure ADVPN via two internet underlays. The requirement is that you use one interface with a single IP address on DC FortiGate.
In this scenario, which feature should be implemented to achieve this requirement?
A. Use network-overlay id
B. Change advpn2 to IKEv1
C. Use local-id
D. Use peer-id
Refer to the exhibits.
Exhibit A
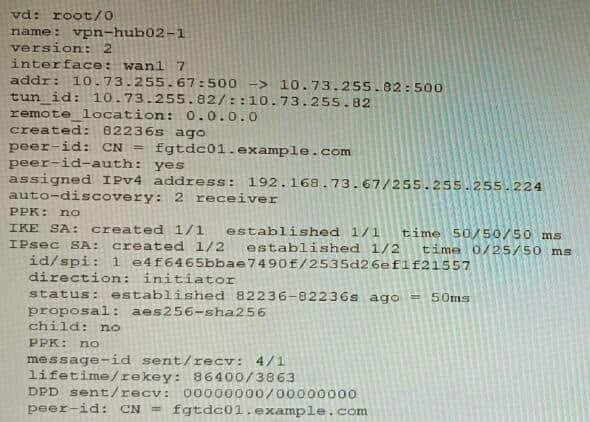
Exhibit B

Exhibit C
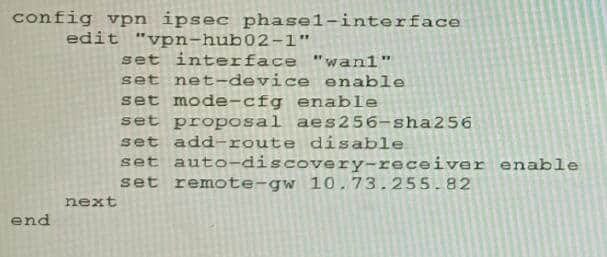
A customer is trying to set up a VPN with a FortiGate, but they do not have a backup of the configuration. Output during a troubleshooting session is shown in the exhibits A and B and a baseline VPN configuration is shown in Exhibit C Referring to the exhibits, which configuration will restore VPN connectivity?
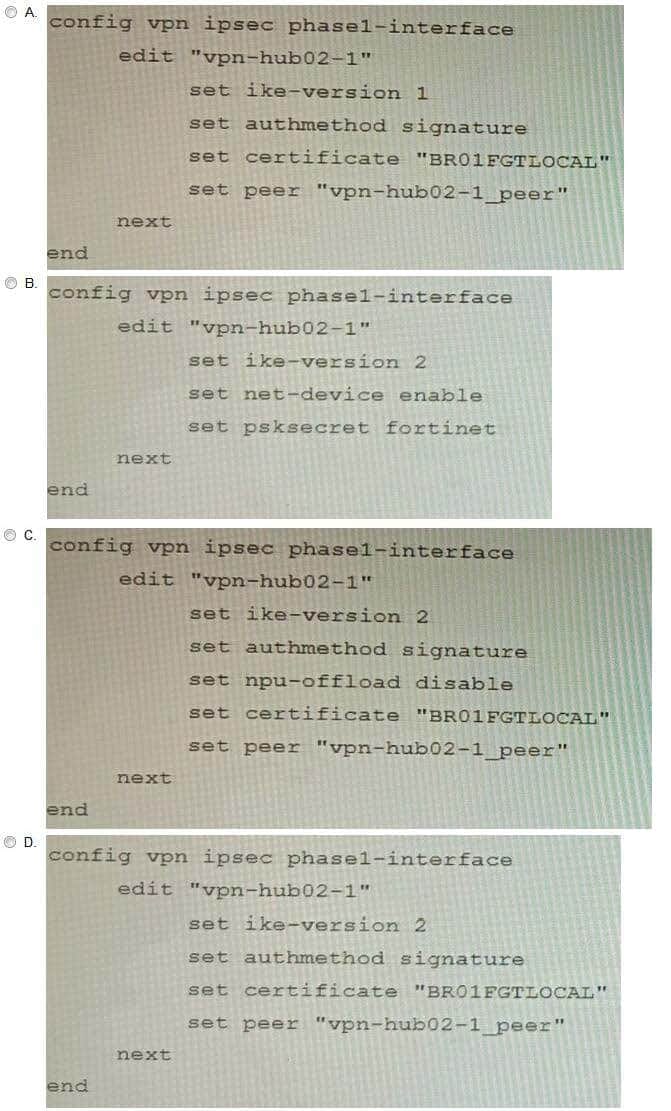
A. Option A
B. Option B
C. Option C
D. Option D
Refer to the exhibit, which shows the high availability configuration for the FortiAuthenticator (FAC1).
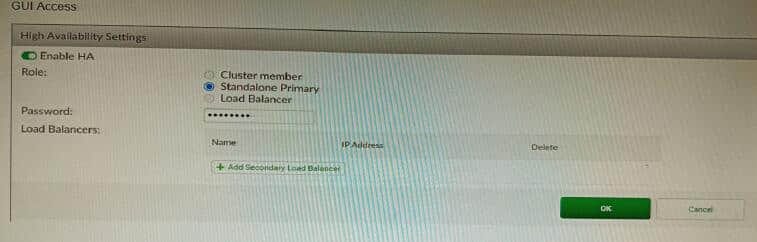
Based on this information, which statement is true about the next FortiAuthenticator (FAC2) member that will join an HA cluster with this FortiAuthenticator (FAC1)?
A. FAC2 can only process requests when FAC1 fails.
B. FAC2 can have its HA interface on a different network than FAC1.
C. The FortiToken license will need to be installed on the FAC2.
D. FSSO sessions from FAC1 will be synchronized to FAC2.
Refer to the exhibit showing an SD-WAN configuration. According to the exhibit, if an internal user pings 10.1.100.2 and 10.1.100.22 from subnet 172.16.205.0/24, which outgoing interfaces will be used?
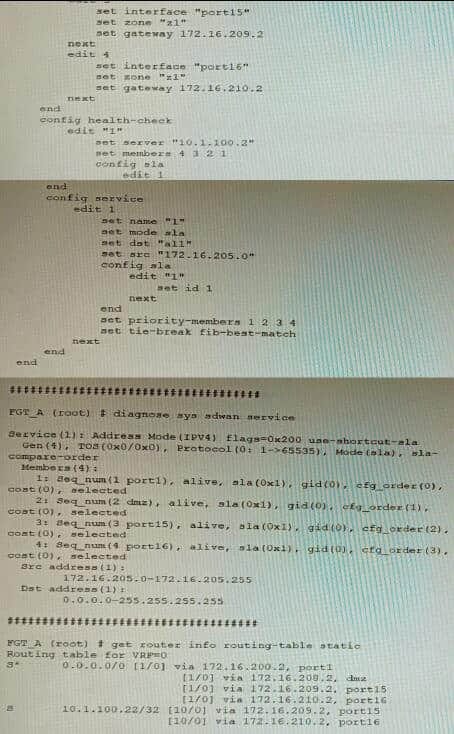
A. port16 and port1
B. port1 and port1
C. port16 and port15
D. port1 and port15
You are deploying a FortiExtender (FEX) on a FortiGate-60F. The FEX will be managed by the FortiGate. You anticipate high utilization. The requirement is to minimize the overhead on the device for WAN traffic.
Which action achieves the requirement in this scenario?
A. Add a switch between the FortiGate and FEX.
B. Enable CAPWAP connectivity between the FortiGate and the FortiExtender.
C. Change connectivity between the FortiGate and the FortiExtender to use VLAN Mode
D. Add a VLAN under the FEX-WAN interface on the FortiGate.
An automation stitch was configured using an incoming webhook as the trigger named 'my_incoming_webhook'. The action is configured to execute the CLI Script shown:
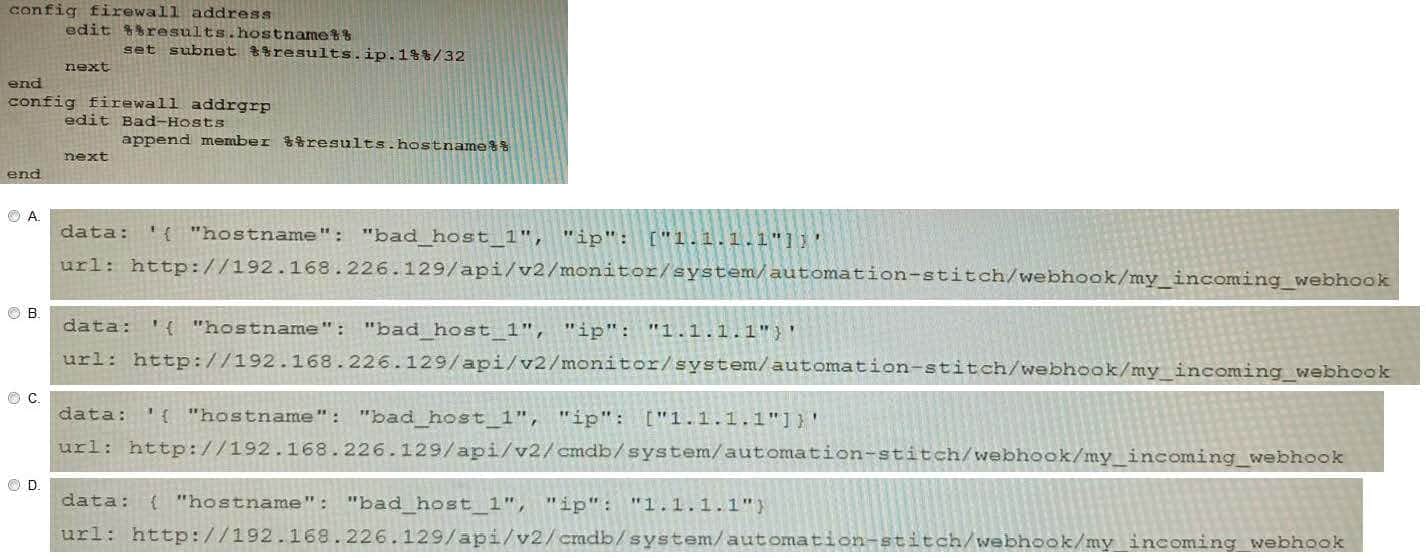
A. Option A
B. Option B
C. Option C
D. Option D

