JPR-961 Online Practice Questions and Answers
You have recently added a Windows Server Web Edition system to your company's private network. The server is used to host the company's private Web site. Users are complaining that response time is often slow. You want to analyze the
traffic coming to and from the Web server.
What should you do?
A. Open Task Manager and use the Networking tab to gather network statistics.
B. Open System Monitor to capture and analyze network traffic.
C. Open Network Diagnostics to analyze the traffic coming to and from the Web server.
D. Install Network Monitor on the Web server to capture and analyze network traffic.
You are the security administrator for your company. The company's network supports 500 users. All network server computers run Windows Server. All network client computers run Windows XP Professional. All domain account logon
events are audited.
A human resources manager requests that you produce a listing of the times and dates a user named JohnP logged on to the domain. The user was assigned to a client computer named HR09.
You should achieve this objective while reviewing the minimum amount of information. What should you do? (Choose two. Each correct answer presents part of the solution.)
A. Create a filter that will list all events for the JohnP user account.
B. Use the Find option to list only the events for the JohnP user account.
C. Open Event Viewer and access the security log on each domain controller.
D. Use the Find option to list only the events for the HR09 computer account.
E. Create a filter that will list only the events for the HR09 computer account.
F. Log onto HR09 as a local administrator, and open Event Viewer to view the local security log.
You are your company's network administrator. The network consists of a single subnet. All servers run Windows Server. The network is connected to the Internet through a private WAN link. A computer named Server1 provides Internet
access for the network. Server1 is equipped with two NICs, and Internet Connection Sharing (ICS) is enabled on the NIC that is connected to the Internet.
Your company employs several telecommuters who work from their homes. The remote employees require some files that contain information about the company's business operations. Those files are updated on a daily basis. To provide the
remote employees with those files, you set up an FTP site on a computer named FTPSrv.
You must ensure that the users on the corporate network can access Internet Web sites and that the remote employees can download the necessary files from FTPSrv. The corporate network must be protected against possible Internet-
based attacks. Access to the corporate network from the Internet must be restricted to only the FTP site on FTPSrv.
What should you do?
A. On FTPSrv, enable Internet Connection Firewall, and specify that FTP traffic be allowed to pass to FTPSrv.
B. On Server1, enable Internet Connection Firewall, and specify that FTP traffic be allowed to pass to FTPSrv.
C. Configure Server1 to use IPSec for all communications on the NIC that is connected to the Internet.
D. On Server1, enable Internet Connection Firewall, and configure it to allow only HTTP and FTP traffic to pass to the corporate network.
Andrew works as a Network Administrator for ABC.com. The company has a Windows domain-based network. The company has two Windows servers and 150 Windows Professional client computers.
The company has a Windows server named NATSERV that has a dial-up connection to the Internet.
NATSERV has two network interfaces named EthernetA and EthernetB .
EthernetA is connected to the LAN and has an IP address of 192.168.1.121. EthernetB is connected to the Internet and has an IP address of 132.103.102.71. The client computers on the LAN connect to the Internet by using NATSERV. NAT
also has Routing and Remote Access installed.
Andrew enables the NAT/Basic Firewall routing protocol on NATSERV. The configuration of the NAT/Basic Firewall routing on NATSERV is shown in the image below:
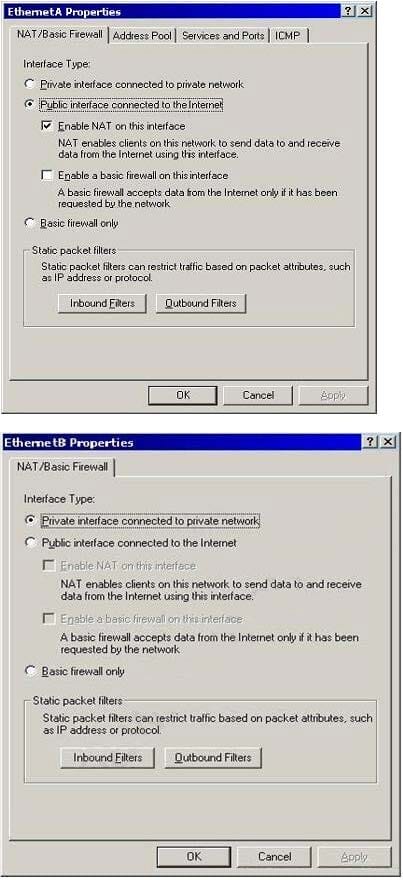
The client computers on the network are unable to connect to the Internet. When Andrew tries to ping
132.103.102.71 from the client computers on the local network, he receives a message as shown in the image below:

Andrew wants to ensure that the client computers on the local network are able to connect to the Internet.
What will he do to accomplish this?
Each correct answer represents a part of the solution. (Choose two.)
A. For EthernetB, configure Outbound Filters under Static packet filters.
B. For EthernetA, configure Inbound Filters under Static packet filters.
C. For EthernetA, configure NAT/Basic Firewall as 'Private interface connected to private network'.
D. For EthernetB, configure NAT/Basic Firewall as 'Public interface connected to the Internet'.
Your corporate network uses variable length subnetting to make more efficient use of IP addresses. One of the IP addresses for a host is 131.39.161.17 with a subnet mask of 255.255.248.0. What is the proper notation for the network to which this host is connected?
A. 131.39.160.0/21
B. 131.36.161.0/20
C. 131.39.161.17/21
D. 131.36.160.0/20
You work as a network administrator for ABC.com. The ABC.com network consists of a single Active Directory domain named ABC.com. There are currently 120 Web servers running Windows Server and are contained in an Organizational Unit (OU) named ABC_WebServers
ABC.com management took a decision to uABCrade all Web servers to Windows Server. You disable all services on the Web servers that are not required. After running the IIS Lockdown Wizard on a recently deployed web server, you discover that services such as NNTP that are not required are still enabled on the Web server.
How can you ensure that the services that are not required are forever disabled on the Web servers without affecting the other servers on the network? (Choose two.)
A. Set up a GPO that will change the startup type for the services to Automatic.
B. By linking the GPO to the ABC_WebServers OU.
C. Set up a GPO with the Hisecws.inf security template imported into the GPO.
D. By linking the GPO to the domain.
E. Set up a GPO in order to set the startup type of the redundant services to Disabled.
F. By linking the GPO to the Domain Controllers OU.
G. Set up a GPO in order to apply a startup script to stop the redundant services.
You are an Enterprise administrator for ABC.com. All servers on the corporate network run Windows Server and all client computers run Windows XP.
The network contains a server named ABC-SR01 that has Routing and Remote Access service and a modem installed which connects to an external phone line.
A partner company uses a dial-up connection to connect to ABC-SR01 to upload product and inventory information. This connection happens between the hours of 1:00am and 2:00am every morning and uses a domain user account to log on
to ABC-SR01.
You have been asked by the security officer to secure the connection.
How can you ensure that the dial-up connection is initiated only from the partner company and that access is restricted to just ABC-SR01? (Choose three.)
A. Set up the log on hours restriction for the domain user account to restrict the log on to between the hours of 1:00am and 2:00am.
B. Set up a local user account on ABC-SR01. Have the dial-up connection configured to log on with this account.
C. Set up the remote access policy on ABC-SR01 to allow the connection for the specified user account between the hours of 1:00am and 2:00am.
D. Set up the remote access policy with the Verify Caller ID option to only allow calling from the phone number of the partner company modem.
E. Set up the remote access policy to allow access to the domain user account only.
You are working as the administrator at ABC.com. The network consists of a single Active Directory domain named ABC.com with the domain functional level set at Windows Server. All network servers run Windows Server and all client computers run Windows XP Professional.
The ABC.com domain is divided into organizational units (OU). All the resource servers are contained in an OU named ABC_SERVERS and the workstations are contained in an OU named ABC_CLIENTS. All resource servers operate at near capacity during business hours. All workstations have low resource usage during business hours.
You received instructions to configure baseline security templates for the resource servers and the workstations. To this end you configured two baseline security templates named ABC_SERVERS.inf and ABC_CLIENTS.inf respectively. The ABC_SERVERS.inf template contains many configuration settings. Applying the ABC_SERVERS.inf template would have a performance impact on the servers. The ABC_CLIENTS.inf contains just a few settings so applying this template would not adversely affect the performance of the workstations.
How would you apply the security templates so that the settings will be periodically enforced whilst ensuring that the solution reduces the impact on the resource servers? (Choose three.)
A. By setting up a GPO named SERVER-GPO and link it to the ABC_SERVERS OU.
B. By having the ABC_SERVERS.inf template imported into SERVER-GPO.
C. By having the ABC_SERVERS.inf and the ABC_CLIENTS.inf templates imported into the Default Domain Policy GPO.
D. By scheduling SECEDIT on each resource server to regularly apply the ABC_SERVERS.inf settings during off-peak hours.
E. By having a GPO named CLIENT-GPO created and linked to the ABC_CLIENTS OU.
F. By having the ABC_CLIENTS.inf template imported into CLIENT-GPO.
G. By having SERVER-GPO and CLIENT-GPO linked to the domain.
The ABC.com network consists of a single Active Directory domain named ABC.com. All servers on the ABC.com network run Windows Server and all client computers run Windows XP Professional.
ABC.com contains a file server named ABC-SR24. ABC-SR24 hosts the home folders for all ABC.com users.
After about a month the ABC.com users raised complaints regarding the unacceptable long time their home folder takes to open at certain times during the day.
You need to determine the reason for the poor performance. You verify that the processor and memory usage is low. You suspect the hard disk may be the cause of the bottleneck.
How would you verify that the hard disk is the problem?
A. Use System Monitor to view the LogicalDisk and PhysicalDisk counters during a period of poor performance.
B. Use Task Manager to view the page faults counter.
C. Configure Auditing on the home folders.
D. Use Network Monitor to view the amount of network traffic to and from the server.
The ABC.com network consists of a single Active Directory domain named ABC.com. ABC.com has its headquarters in Chicago and several branch offices at various locations throughout the country. All servers on the ABC.com network run
Windows Server.
You are in the process of configuring a VPN connection between the Chicago office and a branch office in Dallas using Windows Server computers running Routing and Remote Access (RRAS).
A ABC.com written security policy states that the requirements below must be met:
Data transmitted over the VPN must be encrypted with end to end encryption.
The VPN connection authentication should be at the computer level rather than at user level and with no credential information transmitted over the internet.
How should you configure the VPN? (Choose two.)
A. Use a PPTP connection.
B. Use EAP-TLS authentication.
C. Use a PPP connection.
D. Use MS-CHAP v2 authentication.
E. Use MS-CHAP authentication.
F. Use PAP authentication.
G. Use an L2TP/IPSec connection.

