JN0-541 Online Practice Questions and Answers
Exhibit:
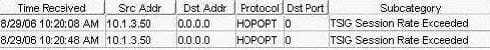
You work as an administrator at Certkiller .com. Study the exhibit carefully. In the exhibit, which rule base would have generated the log message?
A. traffic anomaly
B. backdoor
C. networkhoneypot
D. SYN protector
You can remotely administer the IDP sensor using which two methods? (Choose two.)
A. theWebUI ACM over HTTPS
B. theWebUI ACM over HTTP
C. an SSH connection
D. a telnet connection
Which two statements are true? (Choose two.)
A. If the source IP, target IP, and service in a packet match a particular IDP rule, the rule's action will be performed.
B. All of the rules in the IDPrulebase are examined until either the end of the list is reached, or a matching rule has the Terminate Match button checked.
C. One packet can match on multiple IDP rules.
D. Once the IDP sensor stops comparing a packet against the list of IDP rules, it performs only the first action in the matching rules.
What contains instructions on how the sensor should decode protocols?
A. PCAP files
B. policy.set
C. detector.o
D. ACM
What does the action "drop packet" instruct the sensor to do?
A. Drop the specific session containing the attack pattern.
B. Drop any packet matching this source IP, destination IP, and service.
C. Drop all packets from the attacker's IP address.
D. Drop only the specific packet matching the attack object.
If an IDP sensor finds that a packet matchesa particular IDP rule, and then finds a matching exempt rule, what does the sensor do?
A. Creates a log entry for the matching rule, performs the action in the IDP rule, and then examines the next IDP rule in the list.
B. Does not create a log entry, does not perform the action in the matching rule, and then examines the next IDP rule in the list.
C. Creates a log entry for the matching rule, does not perform the action in the IDP rule, and then examines the next IDP rule in the list.
D. Does not create a log entry or perform the action in the matching rule, and then stops examining the remainder of the IDP rules for that particular packet.
Given the following steps:
a.
Attach the sensor to the management network.
b.
Place the sensor inline in network.
c.
Create and install a policy on the sensor.
d.
Establish communication between Security Manager and the IDP sensor.
e.
Configure the sensor deployment mode and management interface IP.
f.
Test connectivity through the sensor.
Which order is correct when initially deploying a sensor in a network?
A. b, f, e, a, d, c
B. e, a, d, c, b, f
C. a, e, d, c, f, b
D. e, a, d, b, f, c
Which statement is true about reverting Security Policies?
A. The Security Policy cannot be reverted.
B. The Security Policy can be reverted from the ACM of each IDP Sensor.
C. The Security Policy can be reverted at any time from the IDP User interface to a previously installed policy.
D. If you save a copy of your Security Policy from the IDP Sensor, you can revert back by loading the previous copy from the CLI.
Which three actions must be taken prior to deploying an IDP Sensor in a network? (Choose three.)
A. An IP address must be defined on all forwarding interfaces.
B. IDP Sensor must be configured with the ACM and assigned a Management IP address.
C. A Security Policy must be configured for this IDP Sensor.
D. The IDP Sensor object must be configured in the IDP Management Server.
Log Investigator identified 26 attacks from a specific source to a specific destination. How can you view the details of these 26 attacks?
A. go to the Log Viewer and filter that specific source and destination address
B. right-click on the 26 value, select View by Key
C. go to the Log Investigator and filter that specific source and destination address
D. right-click on the 26 value, select View in Log Viewer

