JN0-334 Online Practice Questions and Answers
When considering managed sessions, which configuration parameter determines how full the session table must be to implement the early age-out function?
A. session service timeout
B. high waremark
C. low watermark
D. policy rematch
Click the Exhibit button.
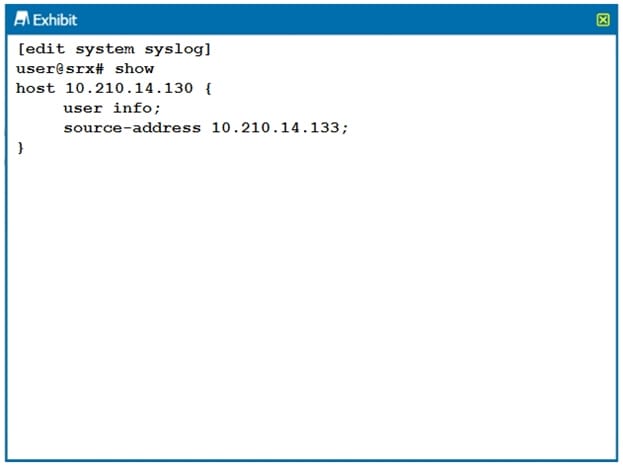
Referring to the configuration shown in the exhibit, which two statements are true? (Choose two.)
A. The log is being stored on the local Routing Engine.
B. The log is being sent to a remote server.
C. The syslog is configured for a user facility.
D. The syslog is configured for an info facility.
A routing change occurs on an SRX Series device that involves choosing a new egress interface. In this scenario, which statement is true for all affected current sessions?
A. The current session are torn down only if the policy-rematchoption has been enabled.
B. The current sessions do not change.
C. The current sessions are torn down and go through first path processing based on the new route.
D. The current sessions might change based on the corresponding security policy.
Click the Exhibit button.
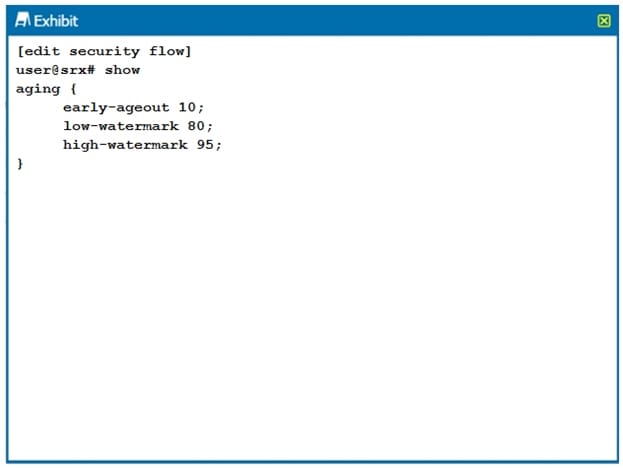
Which two statements are true about the configuration shown in the exhibit? (Choose two.)
A. The session is removed from the session table after 10 seconds of inactivity.
B. The session is removed from the session table after 10 milliseconds of inactivity.
C. Aggressive aging is triggered if the session table reaches 95% capacity.
D. Aggressive aging is triggered if the session table reaches 80% capacity.
Which feature supports sandboxing of zero-day attacks?
A. Sky ATP
B. SSL proxy
C. ALGs
D. high availability
Which two protocols are supported for Sky ATP advanced anti-malware scanning? (Choose two.)
A. POP3
B. MAPI
C. IMAP
D. SMTP
Which two session parameters would be used to manage space on the session table? (Choose two.)
A. low watermark
B. high watermark
C. TCP MSS
D. TCP RST
Which default protocol and port are used for JIMS to SRX client communication?
A. WMI over TCP; port 389
B. ADSI over TCP; port 389
C. HTTPS over TCP: port 443
D. RPC over TCP, port 135
Which two statements about JIMS high availability are true? (Choose two.)
A. JIMS supports high availability through the installation of the primary and secondary JIMS servers.
B. SRX clients are configured with the shared virtual IP (VIP) address of the JIMS server.
C. SRX clients are configured with the unique IP addresses of the primary and secondary JIMS servers.
D. SRX clients synchronize authentication tables with both the primary and secondary JIMS servers.
You want to support reth LAG interfaces on a chassis cluster.
What must be enabled on the interconnecting switch to accomplish this task?
A. RSTP
B. 802.3ad
C. LLDP
D. swfab

