HPE6-A78 Online Practice Questions and Answers
A company is deploying ArubaOS-CX switches to support 135 employees, which will tunnel client traffic to an Aruba Mobility Controller (MC) for the MC to apply firewall policies and deep packet inspection (DPI). This MC will be dedicated to receiving traffic from the ArubaOS-CX switches.
What are the licensing requirements for the MC?
A. one AP license per-switch
B. one PEF license per-switch
C. one PEF license per-switch. and one WCC license per-switch
D. one AP license per-switch. and one PEF license per-switch
What is one way that WPA3-PerSonal enhances security when compared to WPA2- Personal?
A. WPA3-Perscn3i is more secure against password leaking Because all users nave their own username and password
B. WPA3-Personai prevents eavesdropping on other users' wireless traffic by a user who knows the passphrase for the WLAN.
C. WPA3-Personai is more resistant to passphrase cracking Because it requires passphrases to be at least 12 characters
D. WPA3-Personal is more complicated to deploy because it requires a backend authentication server
From which solution can ClearPass Policy Manager (CPPM) receive detailed information about client device type OS and status?
A. ClearPass Onboard
B. ClearPass Access Tracker
C. ClearPass OnGuard
D. ClearPass Guest
A company with 382 employees wants to deploy an open WLAN for guests. The company wants the experience to be as follows:

The company also wants to provide encryption for the network for devices mat are capable, you implement Tor the WLAN.
Which security options should?
A. WPA3-Personal and MAC-Auth
B. Captive portal and WPA3-Personai
C. Captive portal and Opportunistic Wireless Encryption (OWE) in transition mode
D. Opportunistic Wireless Encryption (OWE) and WPA3-Personal
What are some functions of an AruDaOS user role?
A. The role determines which authentication methods the user must pass to gain network access
B. The role determines which firewall policies and bandwidth contract apply to the clients traffic
C. The role determines which wireless networks (SSiDs) a user is permitted to access
D. The role determines which control plane ACL rules apply to the client's traffic
What is an Authorized client as defined by ArubaOS Wireless Intrusion Prevention System (WIP)?
A. a client that has a certificate issued by a trusted Certification Authority (CA)
B. a client that is not on the WIP blacklist
C. a client that has successfully authenticated to an authorized AP and passed encrypted traffic
D. a client that is on the WIP whitelist.
Which correctly describes a way to deploy certificates to end-user devices?
A. ClearPass Onboard can help to deploy certificates to end-user devices, whether or not they are members of a Windows domain
B. ClearPass Device Insight can automatically discover end-user devices and deploy the proper certificates to them
C. ClearPass OnGuard can help to deploy certificates to end-user devices, whether or not they are members of a Windows domain
D. in a Windows domain, domain group policy objects (GPOs) can automatically install computer, but not user certificates
Refer to the exhibit.
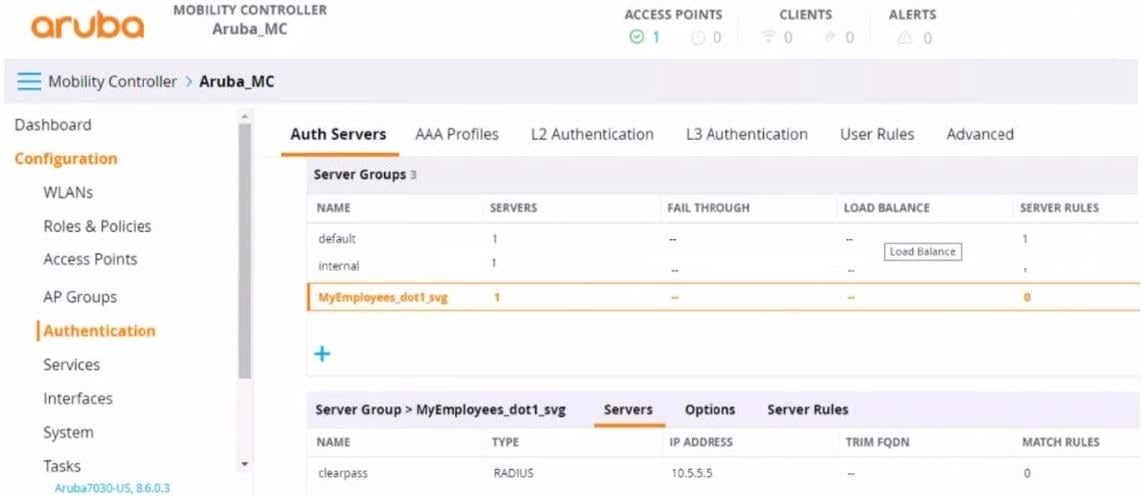
You have set up a RADIUS server on an ArubaOS Mobility Controller (MC) when you created a WLAN named "MyEmployees .You now want to enable the MC to accept change of authorization (CoA) messages from this server for wireless sessions on this WLAN.
What Is a part of the setup on the MC?
A. Create a dynamic authorization, or RFC 3576, server with the 10.5.5.5 address and correct shared secret.
B. Install the root CA associated with the 10 5.5.5 server's certificate as a Trusted CA certificate.
C. Configure a ClearPass username and password in the MyEmployees AAA profile.
D. Enable the dynamic authorization setting in the "clearpass" authentication server settings.
You configure an ArubaOS-Switch to enforce 802.1X authentication with ClearPass Policy Manager (CPPM) denned as the RADIUS server Clients cannot authenticate You check Aruba ClearPass Access Tracker and cannot find a record of the authentication attempt.
What are two possible problems that have this symptom? (Select two)
A. users are logging in with the wrong usernames and passwords or invalid certificates.
B. Clients are configured to use a mismatched EAP method from the one In the CPPM service.
C. The RADIUS shared secret does not match between the switch and CPPM.
D. CPPM does not have a network device defined for the switch's IP address.
E. Clients are not configured to trust the root CA certificate for CPPM's RADIUS/EAP certificate.
What is one way a noneypot can be used to launch a man-in-the-middle (MITM) attack to wireless clients?
A. it uses a combination or software and hardware to jam the RF band and prevent the client from connecting to any wireless networks
B. it runs an NMap scan on the wireless client to And the clients MAC and IP address. The hacker then connects to another network and spoofs those addresses.
C. it examines wireless clients' probes and broadcasts the SSlDs in the probes, so that wireless clients will connect to it automatically.
D. it uses ARP poisoning to disconnect wireless clients from the legitimate wireless network and force clients to connect to the hacker's wireless network instead.

