HP2-Z33 Online Practice Questions and Answers
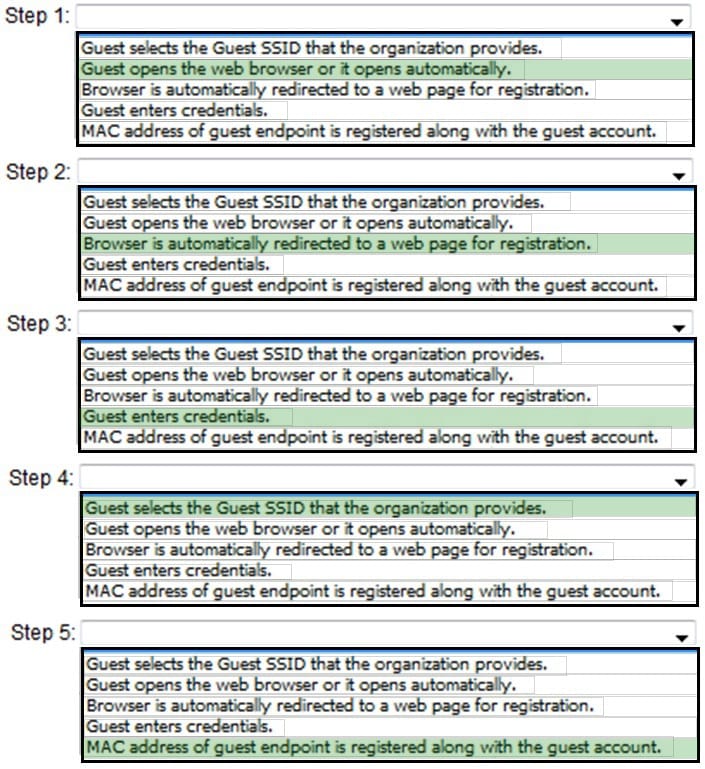
What are the process steps that occur for a guest to access a wireless network managed with an HP BYOD solution? (Place the steps in the correct order.)

Hot Area:

A branch location is deploying standalone wireless access points (APs). What can be used to configure and manage these APs? (Select two.)
A. Access Controller
B. Web interface
C. IMC/UAM
D. IMC/EAD
E. CLI
An organization wants to upgrade their wireless network to allow employees to connect using their 802.11ac enabled devices. Which HP access points meet this requirement?
A. HP 425
B. HPMSM466
C. HP MSM430
D. HP 560
A company decides to use the local portal server function on the HP Unified Wired-WLAN controller. Which rule applies when customizing the default authentication pages?
A. Do not modify the logon failure page.
B. The authentication page files must not exceed 50 MB.
C. Do not change the names of the main authentication page files.
D. Do not compress the authentication page files.
Where can a network administrator check for successful authentication in User Access Manager?
A. User Access Log > Auth Failure Log
B. User Access > LDAP Users
C. User Access Log > Access Details
D. User Access > Access Device Log
In 802.1XEAP-TLS, how can a network administrator control network access of corporate users?
A. by selecting which user groups are entitled to deploy a certificate on their endpoints
B. by selecting which endpoints are entitled to install a certificate
C. by defining corporate users as guests
D. by disabling or deleting the user's endpoint in User Access Manager
What is the maximum data rate that a 2x3 MIMO 802.11 n enabled device can transmit at?
A. 54Mb/s
B. 150 Mb/s
C. 300 Mb/s
D. 450 Mb/s
Which command allows an administrator to access the HP 830 switch CLI from the controller?
A. oap management-ip 192.168.0.101 module 1
B. oap connect slot 0
C. oap management-ip 192.168.0.101 slot 1
D. oap connect module 0
A network administrator is setting up a wireless network secured by 802.1X authentication in EAP mode with an HP BYOD solution. What is an important concept to remember when configuring a Windows laptop to access the wireless network?
A. Root certificates from a Certificate Authority are not needed. The laptop will validate the RADIUS certificate using its client certificate.
B. Do not validate any certificates sent by the RADIUS server. This may cause security issues.
C. User Access Manager can self-generate its own certificate, and this kind of certificate does not need any validation.
D. To automatically validate a certificate sent by User Access Manager (UAM), a client must have a root certificate from the Certificate Authority that issued the UAM certificate
An organization has deployed dual radio access points (APs). They have a mixture of 802.11b, g, and n clients. In this scenario, why is it desirable to steer 802.11n enabled clients to operate in the 5 GHz band?
A. Signals in 5 GHz band propagate further than 2.4 GHz, which enables 802.11n devices to connect at great distances
B. 802.11n can use the higher modulation and coding schemes, which are not allowed in the 2.4 GHz band.
C. When 802.11n devices operate in 2.4 GHz band, they prevent legacy 802.11b.g devices from connecting
D. There are more non-overlapping channels, which increases the probability that channel bonding can be used