GSLC Online Practice Questions and Answers
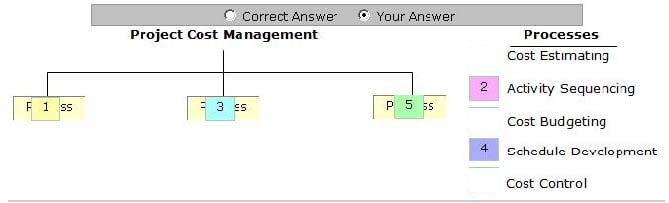
Place the processes that are grouped under the Project Cost Management Knowledge Area in the image below.
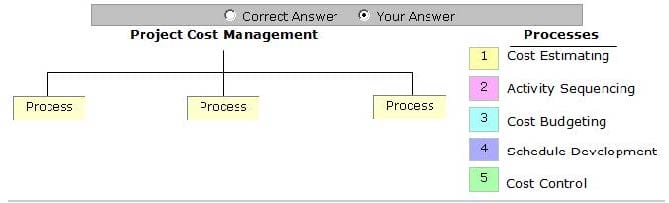
Select and Place:

Which interface does an IPS sensor use to communicate with a security appliance for management purposes?
A. Management interface
B. User interface
C. Command and control interface
D. Monitoring interface
Which of the following types of cryptography algorithms is a symmetric key cipher which operates on fixed-length groups of bits, termed blocks, with an unvarying transformation?
A. RC2
B. Stream cipher
C. Block cipher
D. Triple DES
Which of the following is a computer file used in an operating system to map hostnames to IP addresses?
A. LMHOSTS file
B. NSCD.CONF file
C. TMPFS file
D. HOSTS file
Which of the following tools is a Windows-based commercial wireless LAN analyzer for IEEE 802.11b and supports all high level protocols such as TCP/IP, NetBEUI, and IPX?
A. John the Ripper
B. Cheops-ng
C. AiroPeek
D. Sam Spade
During which of the following processes, probability and impact matrix is prepared?
A. Perform Quantitative Risk Analysis
B. Plan Risk Responses
C. Monitoring and Control Risks
D. Perform Qualitative Risk Analysis
SSH is a network protocol that allows data to be exchanged between two networks using a secure channel. Which of the following encryption algorithms can be used by the SSH protocol? Each correct answer represents a complete solution. Choose all that apply.
A. DES
B. Blowfish
C. IDEA
D. RC4
Which of the following protocols is used as a transport protocol for Internet dial-up connections?
A. SNMP
B. PPP
C. DHCP
D. SMTP
Which of the following is responsible for maintaining certificates in a public key infrastructure (PKI)?
A. Internet Authentication Server
B. Certificate User
C. Certification Authority
D. Domain Controller
Which of the following attributes is a tool that does not aid the project manager in quality planning?
A. Benchmarking practices
B. Design of experiments
C. Media selection
D. Benefit of analysis