GNSA Online Practice Questions and Answers
HOTSPOT
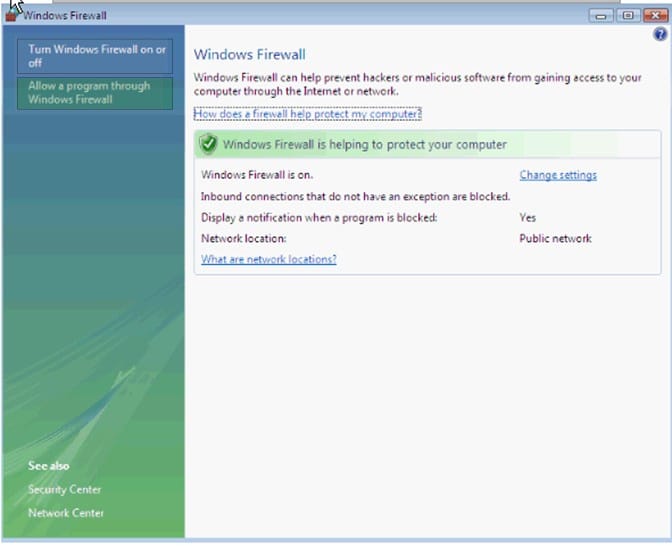
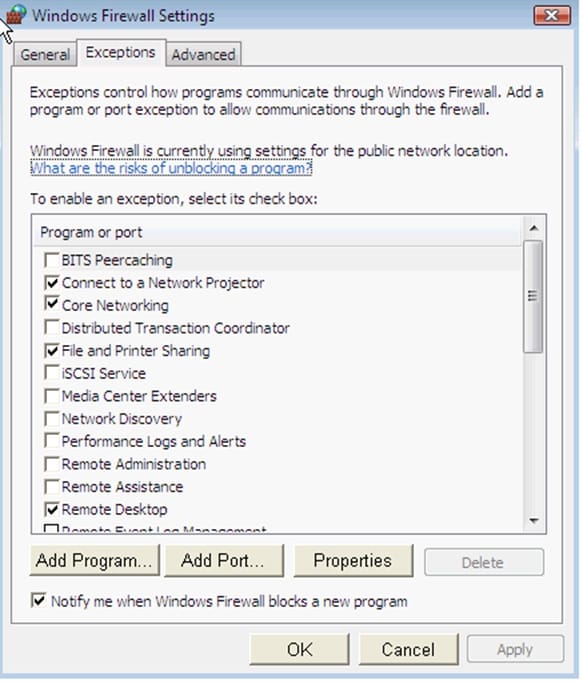
George works as an Office Assistance in TechSoft Inc. All client computers in the company run Windows Vista operating system. He has turned on the Windows Firewall for security purposes. He prepares a document and wants to share it
with other users of the company. When he tries to share the document, he gets a message that firewall has blocked the sharing of the files on his computer. He wants to ensure that that the firewall does not block sharing of the document. He
opens Windows Firewall dialog box.
What actions will he perform in the dialog box to accomplish the task?
Hot Area:
HOTSPOT
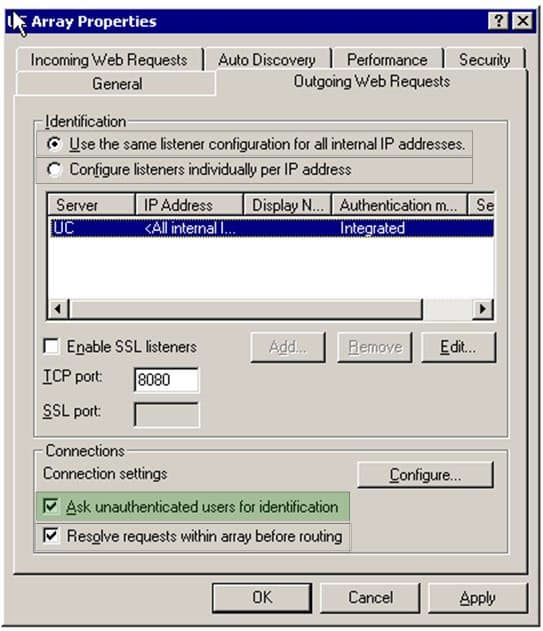
You work as a Network Administrator for uCertify Inc. The company's Windows 2000-based network is configured with Internet Security and Acceleration (ISA) Server 2000. All clients on the network run Windows 2000 Professional. The
company policy prevents you from installing the Firewall Client software or configuring the Web Proxy service on any client computer. You configure access policy rules to allow all the users to use the HTTP protocol for accessing all Internet
sites. However, users on the network report that they are unable to do so.
Mark the option that is configured incorrectly.
Hot Area:
You work as a Network Auditor for XYZ CORP. The company has a Windows-based network. While auditing the company's network, you are facing problems in searching the faults and other entities that belong to it.
Which of the following risks may occur due to the existence of these problems?
A. Residual risk
B. Inherent risk
C. Secondary risk
D. Detection risk
TCP/IP stack fingerprinting is the passive collection of configuration attributes from a remote device during standard layer 4 network communications. The combination of parameters may then be used to infer the remote operating system (OS fingerprinting), or incorporated into a device fingerprint.
Which of the following Nmap switches can be used to perform TCP/IP stack fingerprinting?
A. nmap -sS
B. nmap -sU -p
C. nmap -O -p
D. nmap -sT
Web mining allows a user to look for patterns in data through content mining, structure mining, and usage mining.
What is the function of structure mining?
A. To examine data collected by search engines
B. To examine data collected by Web spiders
C. To examine data related to the structure of a particular Web site
D. To examine data related to a particular user's browser
Which of the following is a technique of using a modem to automatically scan a list of telephone numbers, usually dialing every number in a local area code to search for computers, Bulletin board systems, and fax machines?
A. Warkitting
B. War driving
C. Wardialing
D. Demon dialing
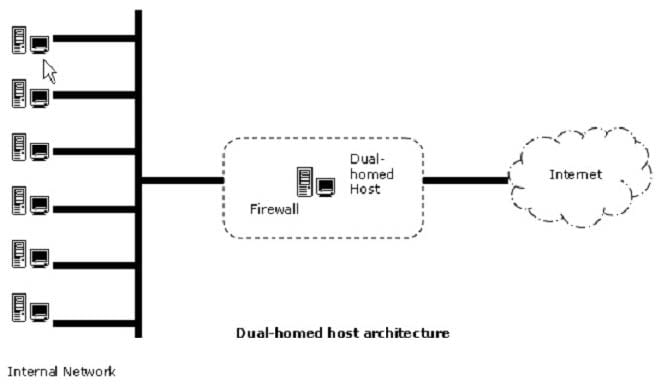
Which of the following are the disadvantages of Dual-Homed Host Firewall Architecture?
A. It can provide services by proxying them.
B. It can provide a very low level of control.
C. User accounts may unexpectedly enable services a user may not consider secure.
D. It provides services when users log on to the dual-homed host directly.
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to identify the list of users with special privileges along with the commands that they can execute.
Which of the following Unix configuration files can you use to accomplish the task?
A. /proc/meminfo
B. /etc/sysconfig/amd
C. /proc/modules
D. /etc/sudoers
Which of the following commands can be used to convert all lowercase letters of a text file to uppercase?
A. tac
B. tr
C. cat
D. less
Fill in the blank with the appropriate command.
You want to search the most recent command that starts with the string 'user'. For this, you will enter the ________ command to get the desired result.
A. history !user