GCIA Online Practice Questions and Answers
Which of the following two cryptography methods are used by NTFS Encrypting File System (EFS) to encrypt the data stored on a disk on a file-by-file basis?
A. Public key
B. Digital certificates
C. Twofish
D. RSA
Which of the following can be configured so that when an alarm is activated, all doors lock and the suspect or intruder is caught between the doors in the dead-space?
A. Man trap
B. Network Intrusion Detection System (NIDS)
C. Biometric device
D. Host Intrusion Detection System (HIDS)
An attacker changes the address of a sub-routine in such a manner that it begins to point to the address of the malicious code. As a result, when the function has been exited, the application can be forced to shift to the malicious code. The image given below explains this phenomenon:
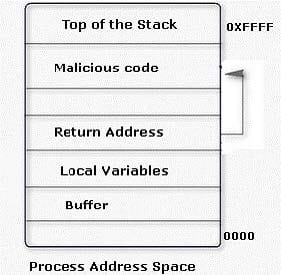
Which of the following tools can be used as a countermeasure to such an attack?
A. Obiwan
B. SmashGuard
C. Kismet
D. Absinthe
Which of the following utilities is used to display the current TCP/IP configuration of a Windows NT computer?
A. NBTSTAT
B. IPCONFIG
C. CONFIG.SYS
D. FTP
Andrew works as an Administrator for a Windows 2000 based network. The network has a primary external DNS server, and a secondary DNS server located on the ISP's UNIX server, in order to provide fault tolerance. Users complain that they are unable to connect to the URL when using the secondary server. What should Andrew do to resolve the problem?
A. He should disable the fast zone transfer in the Advanced tab of the Properties window on the secondary server.
B. He should select the BIND secondaries check box in the Zone Transfer tab of the Properties window on the primary server.
C. He should select the BIND secondaries check box in the Advanced tab of the Properties window on the primary server.
D. He should enable the fast zone transfer in the Advanced tab of the Properties window on the primary server.
Which of the following is an example of penetration testing?
A. Implementing HIDS on a computer
B. Simulating an actual attack on a network
C. Implementing NIDS on a network
D. Configuring firewall to block unauthorized traffic
Which of the following malicious programs changes its signature continuously to be invisible to IDS?
A. Boot sector virus
B. Trojan
C. Malware
D. Polymorphic virus
Which of the following image file formats uses a lossy data compression technique?
A. GIF
B. JPG
C. PNG
D. TIF
Which of the following commands used in Linux to create bit-stream images?
A. ss
B. xcopy
C. dd
D. img
Which of the following is the purpose of creating a Demilitarized zone (DMZ) in an enterprise network?
A. Performing Isolation
B. Creating Autonomous Systems
C. Intrusion Detection
D. Military usage

