GCFA Online Practice Questions and Answers
Maria works as a professional Ethical Hacker. She recently got a project to test the security of www.we-are-secure.com. Arrange the three pre-test phases of the attack to test the security of weare-secure.
You work as a Network Administrator for Net World International. You have configured the hard disk drive of your computer as shown in the image below:
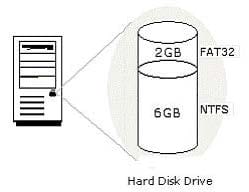
The computer is configured to dual-boot with Windows 2000 Server and Windows 98. While working on Windows 2000 Server, you save a file on the 6GB partition. You are unable to find the file while working on Windows 98. You are not even able to access the partition on which the file is saved. What is the most likely cause?
A. The file is corrupt.
B. The 6GB partition is corrupt.
C. Windows 98 does not support the NTFS file system.
D. Files saved in Windows 98 are not supported by Windows 2000.
Which of the following IP addresses are private addresses?
Each correct answer represents a complete solution. Choose all that apply.
A. 19.3.22.17
B. 192.168.15.2
C. 192.166.54.32
D. 10.0.0.3
Adam works as a professional Computer Hacking Forensic Investigator. He has been called by the FBI to examine data of the hard disk, which is seized from the house of a suspected terrorist. Adam decided to acquire an image of the suspected hard drive. He uses a forensic hardware tool, which is capable of capturing data from IDE, Serial ATA, SCSI devices, and flash cards. This tool can also produce MD5 and CRC32 hash while capturing the data. Which of the following tools is Adam using?
A. Wipe MASSter
B. ImageMASSter 4002i
C. ImageMASSter Solo-3
D. FireWire DriveDock
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate the BlackBerry, which is suspected to be used to hide some important information. Which of the following is the first step taken to preserve the information in forensic investigation of the BlackBerry?
A. Keep BlackBerry in 'ON' state.
B. Remove the storage media.
C. Eliminate the ability of the device to receive the push data.
D. Turn off the BlackBerry.
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him by the chief security officer of a cloth manufacturing company who suspects that one of the employees is selling the design of the clothes outside the company. The security officer asked Adam to investigate the iPhone of the employee, as he suspects that there might be some sensitive information stored in his iPhone. On investigation Adam found out that the employee tries to destroy the evidence on his iPhone. He presses and holds the Home and Power buttons until the device is forced into recovery mode. Which of the following actions occurred when iPhone is set into recovery mode?
A. iPhone will be prevented from booting temporarily.
B. The file system will be destroyed.
C. Nothing will happen.
D. Data will be destroyed.
Which of the following graphical tools is used to navigate through directory structures?
A. Disk Cleanup
B. System Information
C. Disk Management
D. Windows Explorer
Which of the following registry hives stores configuration information specific to a particular user who is currently logged on to the computer?
A. HKEY_USERS
B. HKEY_CURRENT_USER
C. HKEY_LOCAL_MACHINE
D. HKEY_CLASSES_ROOT
Which of the following statements is true for a file in the UNIX operating system?
A. It is a collection of information, which cannot be data or documents.
B. It is a directory entry that points to an original file somewhere else.
C. It is a collection of information, which can be data, an application, or documents.
D. It is a collection of information, which can be only documents.
You work as a Network Administrator for NetTech Inc. To ensure the security of files, you encrypt data files using Encrypting File System (EFS). You want to make a backup copy of the files and maintain security settings. You can backup the files either to a network share or a floppy disk.
What will you do to accomplish this?
A. Place the files in an encrypted folder. Then, copy the folder to a floppy disk.
B. Copy the files to a network share on a FAT32 volume.
C. Copy the files to a network share on an NTFS volume.
D. Copy the files to a floppy disk that has been formatted using Windows 2000 Professional.