GCED Online Practice Questions and Answers
Why would the pass action be used in a Snort configuration file?
A. The pass action simplifies some filtering by specifying what to ignore.
B. The pass action passes the packet onto further rules for immediate analysis.
C. The pass action serves as a placeholder in the snort configuration file for future rule updates.
D. Using the pass action allows a packet to be passed to an external process.
E. The pass action increases the number of false positives, better testing the rules.
When attempting to collect data from a suspected system compromise, which of the following should generally be collected first?
A. The network connections and open ports
B. The contents of physical memory
C. The current routing table
D. A list of the running services
Which of the following is an operational security control that is used as a prevention mechanism?
A. Labeling of assets
B. Heat detectors
C. Vibration alarms
D. Voltage regulators
An analyst will capture traffic from an air-gapped network that does not use DNS. The analyst is looking for unencrypted Syslog data being transmitted. Which of the following is most efficient for this purpose?
A. tcpdump –s0 –i eth0 port 514
B. tcpdump –nnvvX –i eth0 port 6514
C. tcpdump –nX –i eth0 port 514
D. tcpdump –vv –i eth0 port 6514
You have been tasked with searching for Alternate Data Streams on the following collection of Windows partitions; 2GB FAT16, 6GB FAT32, and 4GB NTFS. How many total Gigabytes and partitions will you need to search?
A. 4GBs of data, the NTFS partition only.
B. 12GBs of data, the FAT16, FAT32, and NTFS partitions.
C. 6GBs of data, the FAT32 partition only.
D. 10GBs of data, both the FAT32 and NTFS partitions.
What piece of information would be recorded by the first responder as part of the initial System Description?
A. Copies of log files
B. System serial number
C. List of system directories
D. Hash of each hard drive
The matrix in the screen shot below would be created during which process?
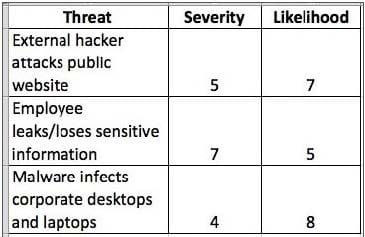
A. Risk Assessment
B. System Hardening
C. Data Classification
D. Vulnerability Scanning
Which of the following is the best way to establish and verify the integrity of a file before copying it during an investigation?
A. Write down the file size of the file before and after copying and ensure they match
B. Ensure that the MAC times are identical before and after copying the file
C. Establish the chain of custody with the system description to prove it is the same image
D. Create hash of the file before and after copying the image verifying they are identical
What would be the output of the following Google search? filetype:doc inurl:ws_ftp
A. Websites running ws_ftp that allow anonymous logins
B. Documents available on the ws_ftp.com domain
C. Websites hosting the ws_ftp installation program
D. Documents found on sites with ws_ftp in the web address
Which tool keeps a backup of all deleted items, so that they can be restored later if need be?
A. ListDLLs
B. Yersinia
C. Ettercap
D. ProcessExplorer
E. Hijack This

