GCCC Online Practice Questions and Answers
Which approach is recommended by the CIS Controls for performing penetration tests?
A. Document a single vulnerability per system
B. Utilize a single attack vector at a time
C. Complete intrusive tests on test systems
D. Execute all tests during network maintenance windows
Which of the following is a responsibility of a change management board?
A. Reviewing log files for unapproved changes
B. Approving system baseline configurations.
C. Providing recommendations for the changes
D. Reviewing configuration of the documents
Which of the following actions would best mitigate against phishing attempts such as the example below?

A. Establishing email filters to block no-reply address emails
B. Making web filters to prevent accessing Google Docs
C. Having employee's complete user awareness training
D. Recommending against the use of Google Docs
Implementing which of the following will decrease spoofed e-mail messages?
A. Finger Protocol
B. Sender Policy Framework
C. Network Address Translation
D. Internet Message Access Protocol
An organization is implementing an application software security control their custom-written code that provides web--based database access to sales partners. Which action will help mitigate the risk of the application being compromised?
A. Providing the source code for their web application to existing sales partners
B. Identifying high-risk assets that are on the same network as the web application server
C. Creating signatures for their IDS to detect attacks specific to their web application
D. Logging the connection requests to the web application server from outside hosts
Which of the following assigns a number indicating the severity of a discovered software vulnerability?
A. CPE
B. CVE
C. CCE
D. CVSS
Acme Corporation performed an investigation of its centralized logging capabilities. It found that the central server is missing several types of logs from three servers in Acme's inventory. Given these findings, what is the most appropriate next step?
A. Define processes to manually review logs for the problem servers
B. Restart or reinstall the logging service on each of the problem servers
C. Perform analysis to identify the source of the logging problems
D. Document the missing logs in the core evaluation report as a minor issue
Review the below results of an audit on a server. Based on these results, which document would you recommend be reviewed for training or updates?

A. Procedure for authorizing remote server access
B. Procedure for modifying file permissions
C. Procedure for adjusting network share permissions
D. Procedure for setting and resetting user passwords
Acme Corporation is doing a core evaluation of its centralized logging capabilities. Which of the following scenarios indicates a failure in more than one CIS Control?
A. The loghost is missing logs from 3 servers in the inventory
B. The loghost is receiving logs from hosts with different timezone values
C. The loghost time is out-of-sync with an external host
D. The loghost is receiving out-of-sync logs from undocumented servers
Based on the data shown below.
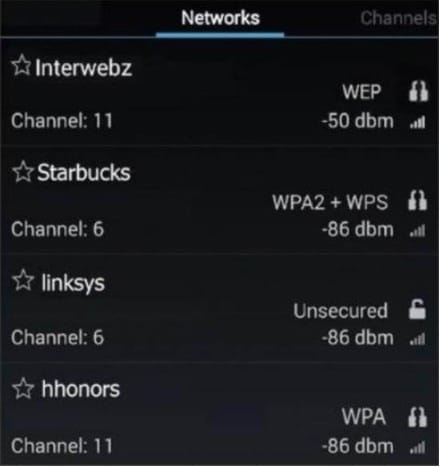
Which wireless access point has the manufacturer default settings still in place?
A. Starbucks
B. Linksys
C. Hhonors
D. Interwebz

