EC1-349 Online Practice Questions and Answers
Meyer Electronics Systems just recently had a number of laptops stolen out of their office. On these laptops contained sensitive corporate information regarding patents and company strategies. A month after the laptops were stolen, a competing company was found to have just developed products that almost exactly duplicated products that Meyer produces. What could have prevented this information from being stolen from the laptops?
A. DFS Encryption
B. EFS Encryption
C. SDW Encryption
D. IPS Encryption
In what way do the procedures for dealing with evidence in a criminal case differ from the procedures for dealing with evidence in a civil case?
A. evidence must be handled in the same way regardless of the type of case
B. evidence procedures are not important unless you work for a law enforcement agency
C. evidence in a criminal case must be secured more tightly than in a civil case
D. evidence in a civil case must be secured more tightly than in a criminal case
When is it appropriate to use computer forensics?
A. If copyright and intellectual property theft/misuse has occurred
B. If employees do not care for their boss?management techniques
C. If sales drop off for no apparent reason for an extended period of time
D. If a financial institution is burglarized by robbers
What feature of Windows is the following command trying to utilize?
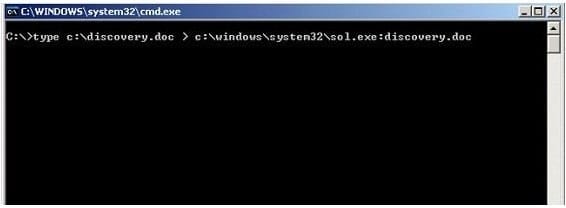
A. White space
B. AFS
C. ADS
D. Slack file
Email archiving is a systematic approach to save and protect the data contained in emails so that it can be accessed fast at a later date. There are two main archive types, namely Local Archive and Server Storage Archive. Which of the following statements is correct while dealing with local archives?
A. It is difficult to deal with the webmail as there is no offline archive in most cases. So consult your counsel on the case as to the best way to approach and gain access to the required data on servers
B. Local archives do not have evidentiary value as the email client may alter the message data
C. Local archives should be stored together with the server storage archives in order to be admissible in a court of law
D. Server storage archives are the server information and settings stored on a local system whereas the
local archives are the local email client information stored on the mail server
Windows Security Event Log contains records of login/logout activity or other security-related events specified by the system's audit policy. What does event ID 531 in Windows Security Event Log indicates?
A. A user successfully logged on to a computer
B. The logon attempt was made with an unknown user name or a known user name with a bad password
C. An attempt was made to log on with the user account outside of the allowed time
D. A logon attempt was made using a disabled account
Cyber-crime is defined as any Illegal act involving a gun, ammunition, or its applications.
A. True
B. False
Hash injection attack allows attackers to inject a compromised hash into a local session and use the hash to validate network resources.
A. True
B. False
When NTFS Is formatted, the format program assigns the __________ sectors to the boot sectors and to the bootstrap code
A. First 12
B. First 16
C. First 22
D. First 24
Digital evidence validation involves using a hashing algorithm utility to create a binary or hexadecimal number that represents the uniqueness of a data set, such as a disk drive or file.
Which of the following hash algorithms produces a message digest that is 128 bits long?
A. CRC-32
B. MD5
C. SHA-1
D. SHA-512

