CISSP-2018 Online Practice Questions and Answers
HOTSPOT
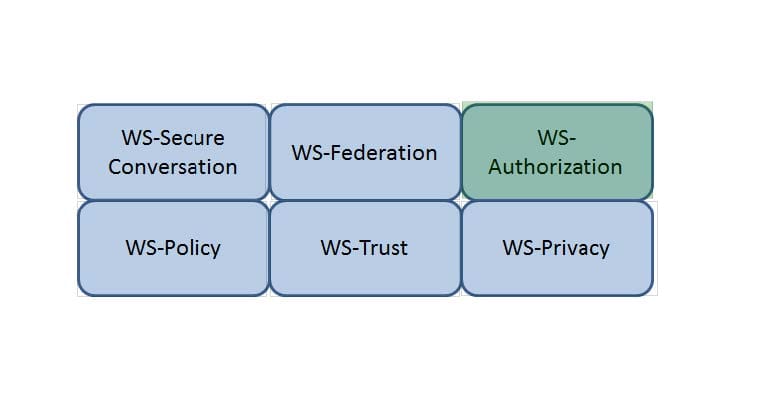
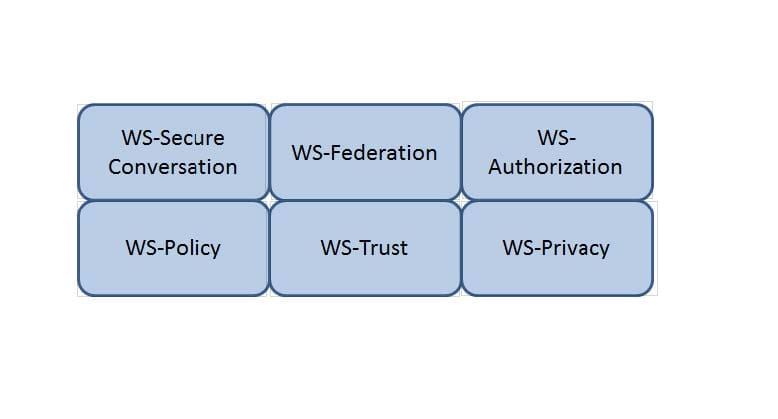
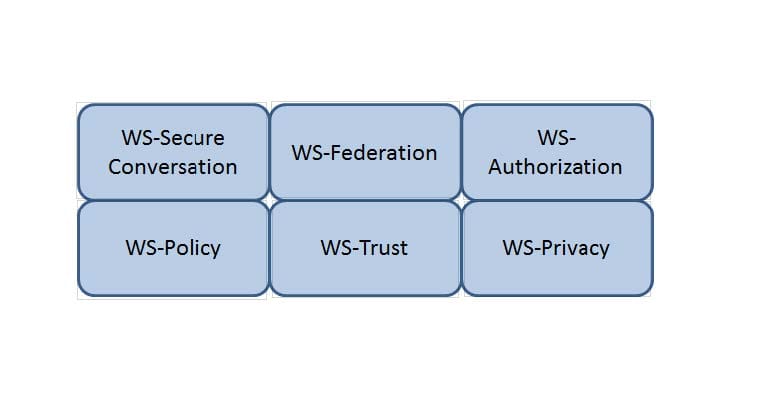
Which Web Services Security (WS-Security) specification handles the management of security tokens and the underlying policies for granting access? Click on the correct specification in the image below.
Hot Area:
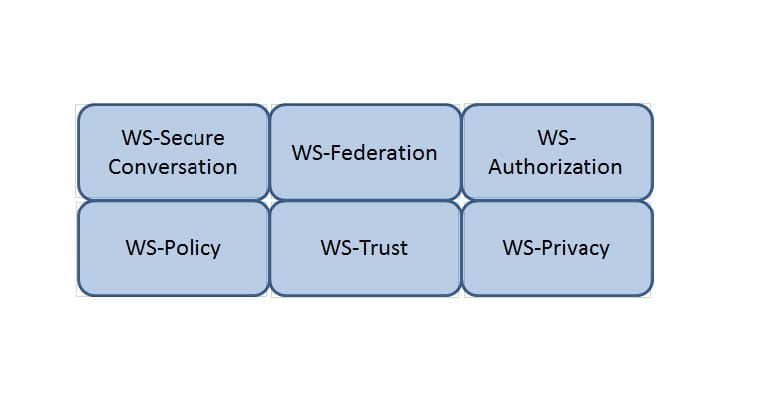
HOTSPOT
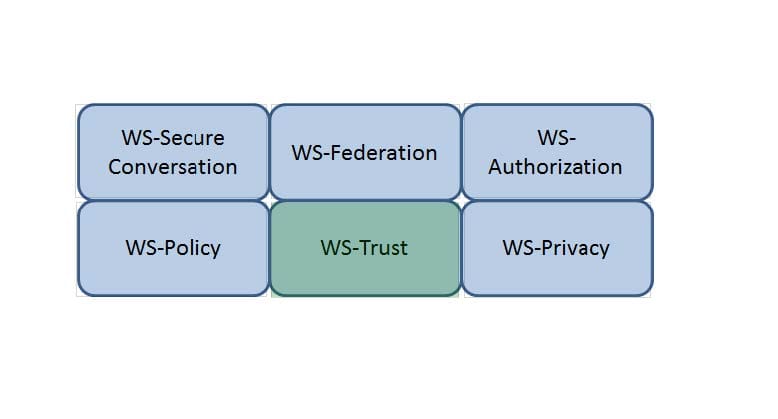
Which Web Services Security (WS-Security) specification negotiates how security tokens will be issued, renewed and validated? Click on the correct specification in the image below.
Hot Area:
HOTSPOT
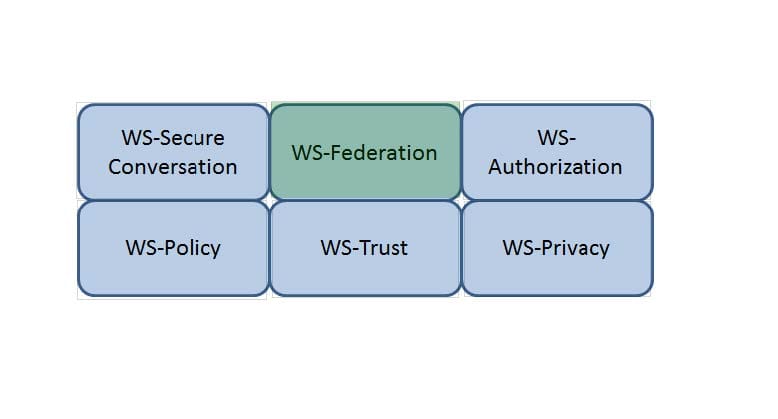
Which Web Services Security (WS-Security) specification maintains a single authenticated identity across multiple dissimilar environments? Click on the correct specification in the image below.
Hot Area:
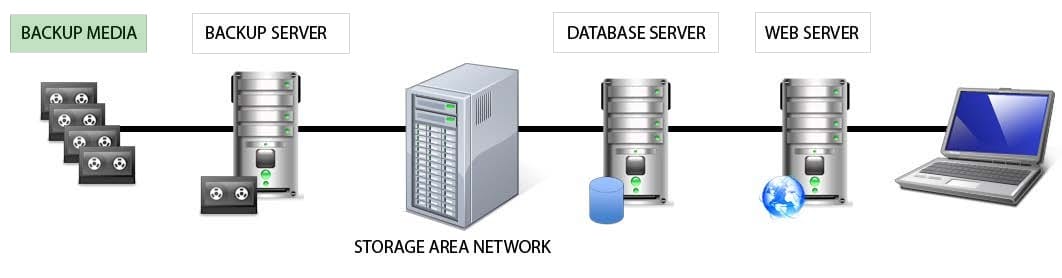
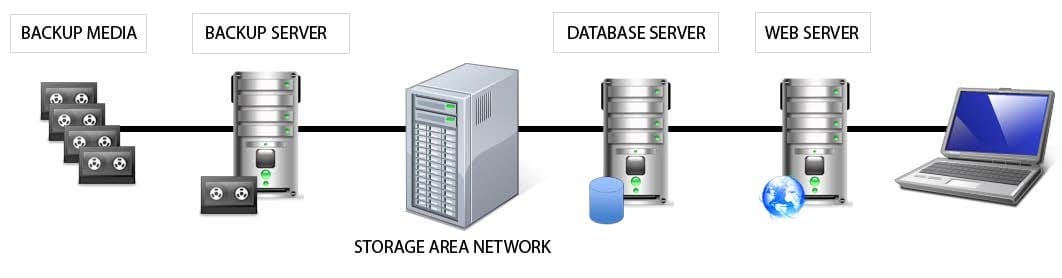
HOTSPOT
Identify the component that MOST likely lacks digital accountability related to information access. Click on the correct device in the image below.
Hot Area:
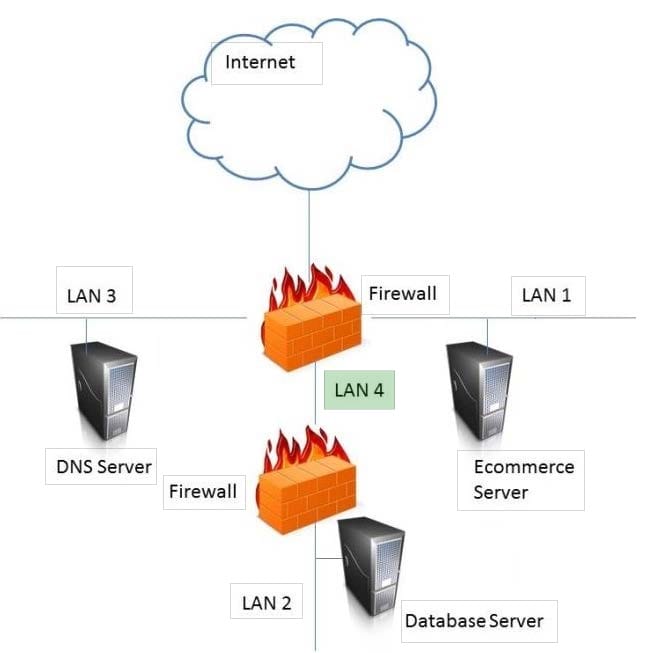
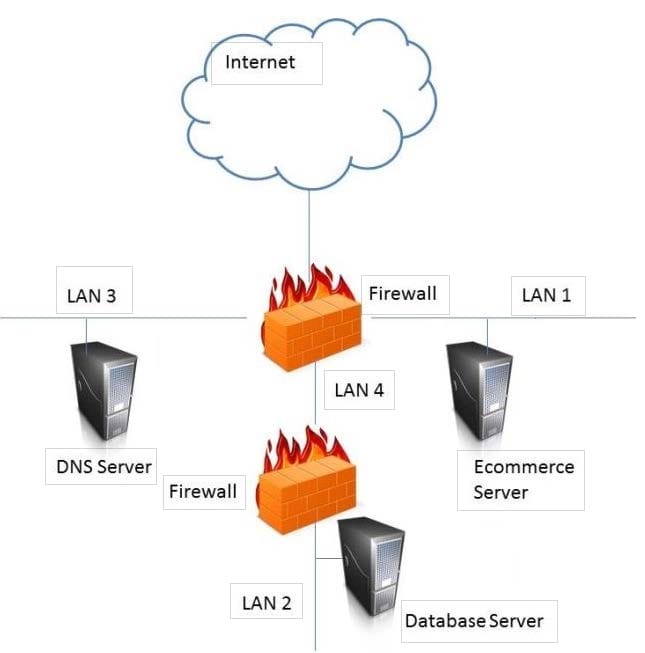
HOTSPOT
In the network design below, where is the MOST secure Local Area Network (LAN) segment to deploy a Wireless Access Point (WAP) that provides contractors access to the Internet and authorized enterprise services?
Hot Area:
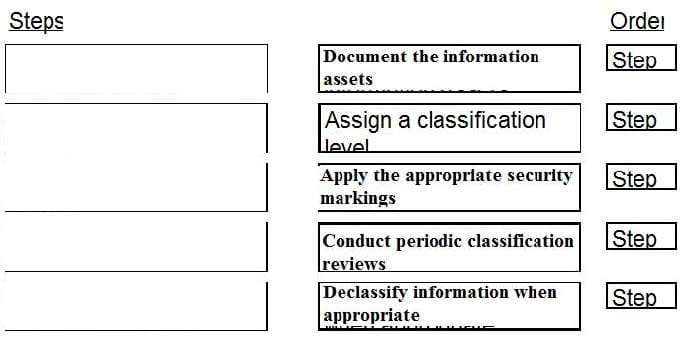
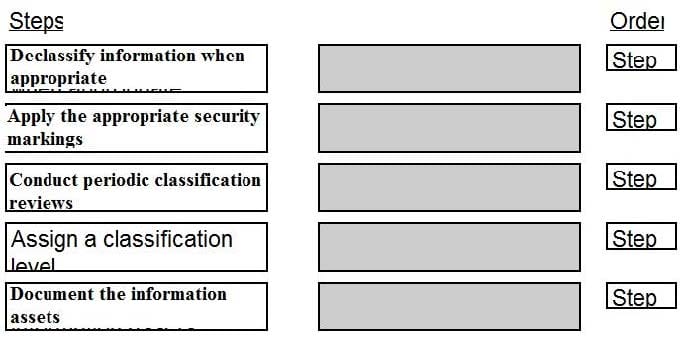
DRAG DROP
Place the following information classification steps in sequential order.
Select and Place:
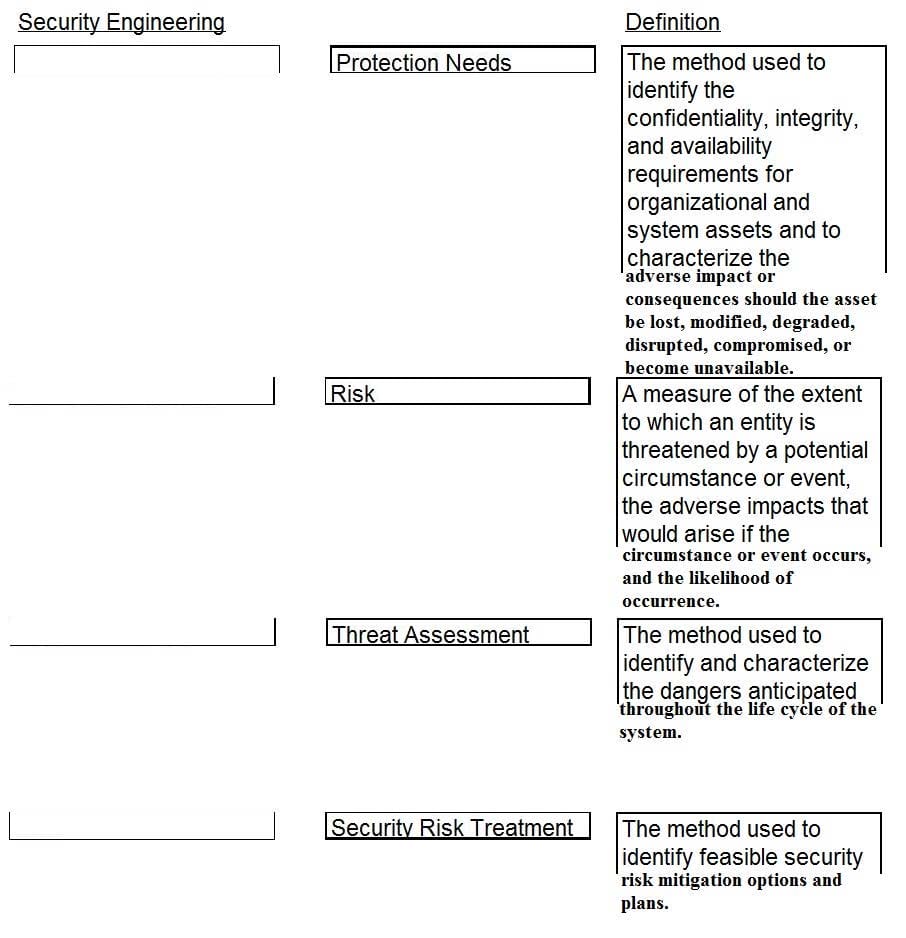
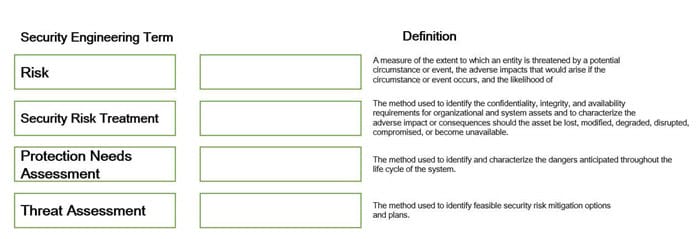
DRAG DROP
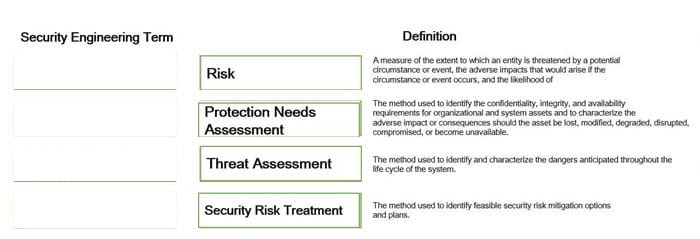
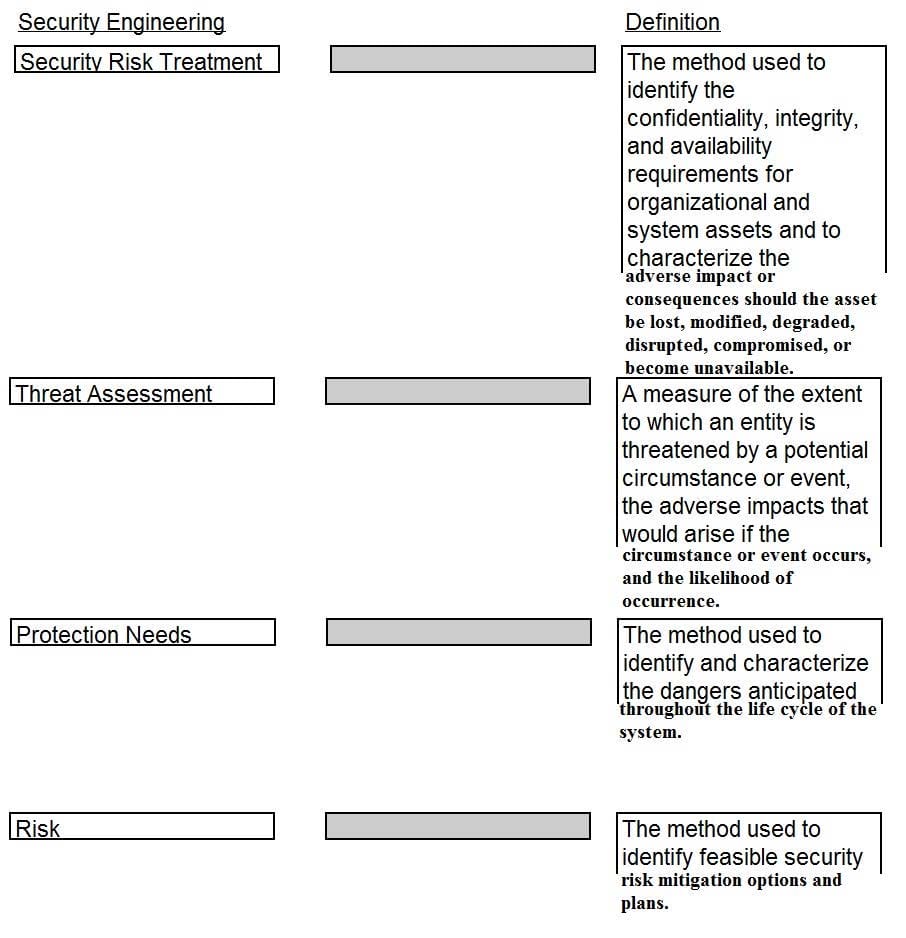
Drag the following Security Engineering terms on the left to the BEST definition on the right.
Select and Place:
DRAG DROP
Match the objectives to the assessment questions in the governance domain of Software Assurance Maturity Model (SAMM).
Select and Place:

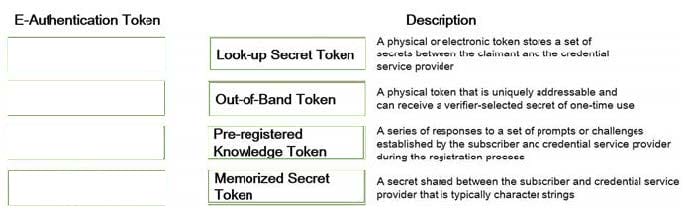
DRAG DROP
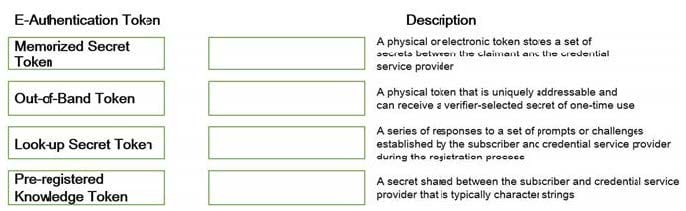
Match the types of e-authentication tokens to their description.
Drag each e-authentication token on the left to its corresponding description on the right.
Select and Place:
DRAG DROP
Drag the following Security Engineering terms on the left to the BEST definition on the right.
Select and Place: