CCST-NETWORKING Online Practice Questions and Answers
During the data encapsulation process, which OSI layer adds a header that contains MAC addressing information and a trailer used for error checking?
A. Network
B. Transport
C. Data Link
D. Session
Examine the following output:
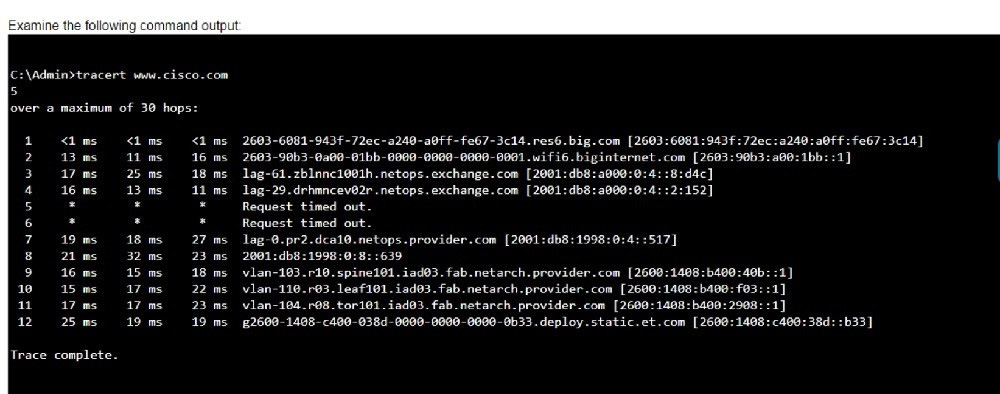
Which two conclusions can you make from the output of the tracert command? (Choose 2.)
Note: You will receive partial credit for each correct answer.
A. The trace successfully reached the www.cisco.com server.
B. The trace failed after the fourth hop.
C. The IPv6 address associated with the www.cisco.com server is 2600:1408: c400: 38d: : b33.
D. The routers at hops 5 and 6 are offline.
E. The device sending the trace has IPv6 address 2600:1408:c400:38d :: b33.
An engineer configured a new VLAN named VLAN2 for the Data Center team. When the teamtries to ping addresses outside VLAN2 from a computer in VLAN2, they are unable to reach them.
What should the engineer configure?
A. Additional VLAN
B. Default route
C. Default gateway
D. Static route
A user initiates a trouble ticket stating that an external web page is not loading. You determine that other resources both internal and external are still reachable.
Which command can you use to help locate where the issue is in the network path to the external web page?
A. ping -t
B. tracert
C. ipconfig/all
D. nslookup
A Cisco PoE switch is shown in the following image. Which type of port will provide both data connectivity and power to an IP phone?

A. Port identified with number 2
B. Ports identified with numbers 3 and 4
C. Ports identified with number 6
D. Ports identified with number 7
Which two pieces of information should you include when you initially create a support ticket? (Choose 2.)
A. A detailed description of the fault
B. Details about the computers connected to the network
C. A description of the conditions when the fault occurs
D. The actions taken to resolve the fault
E. The description of the top-down fault-finding procedure
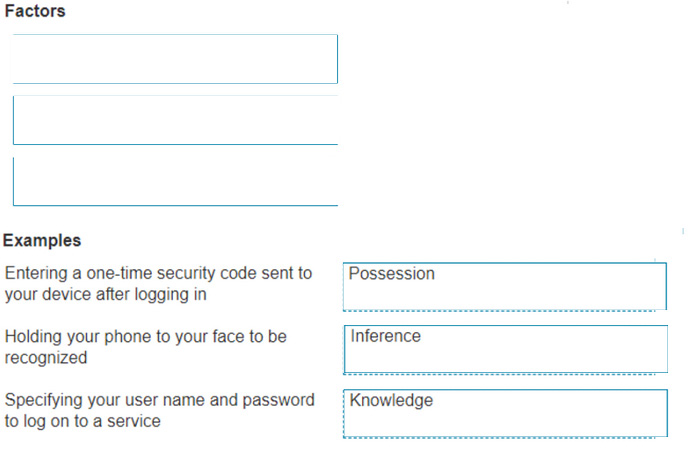
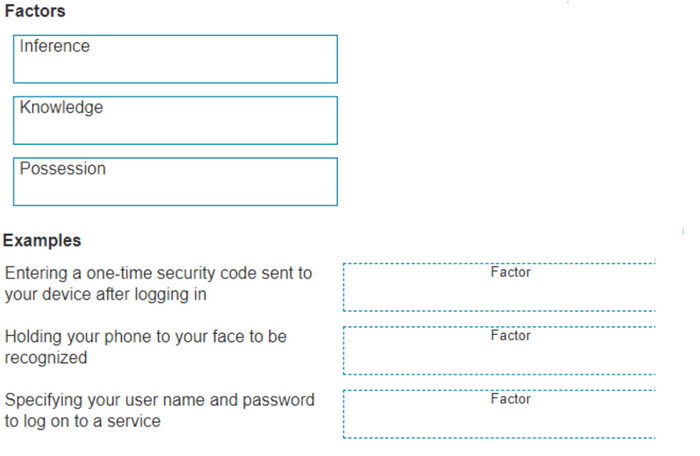
DRAG DROP
Move the MFA factors from the list on the left to their correct examples on the right. You may use each factor once, more than once, or not at all.
Note: You will receive partial credit for each correct selection.
Select and Place:
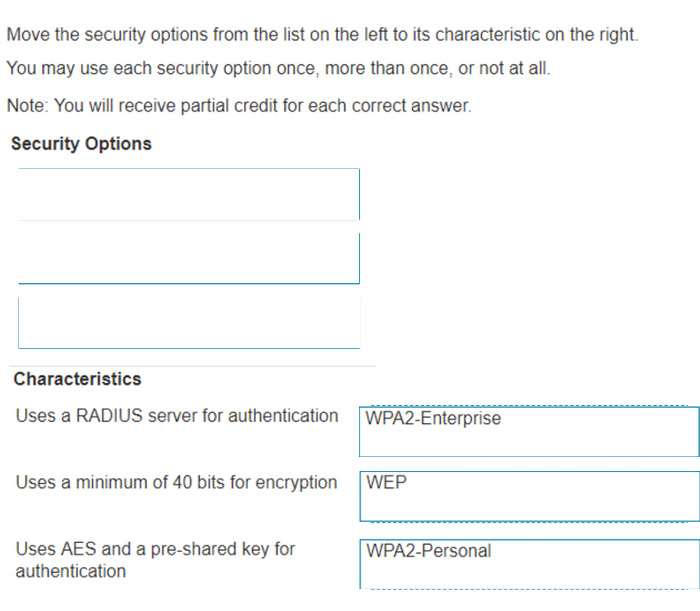
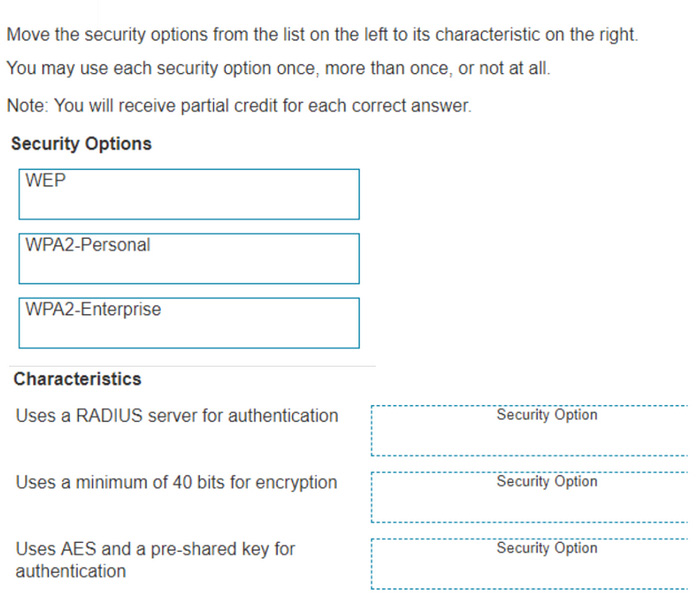
DRAG DROP
Move the security options from the list on the left to its characteristic on the right. You may use each security option once, more than once, or not at all.
Note: You will receive partial credit for each correct answer.
Select and Place:
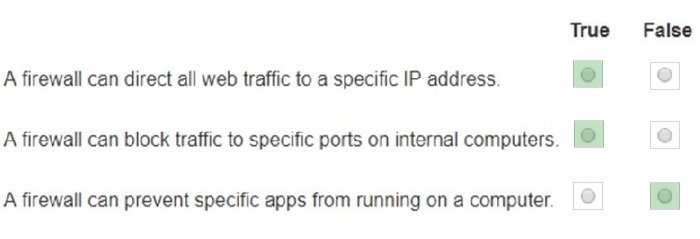
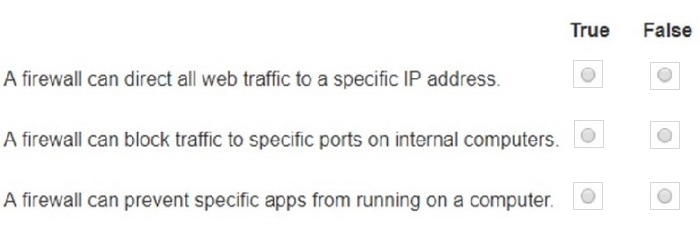
HOTSPOT
You plan to use a network firewall to protect computers at a small office.
For each statement about firewalls, select True or False.
Note: You will receive partial credit for each correct selection.
Hot Area:
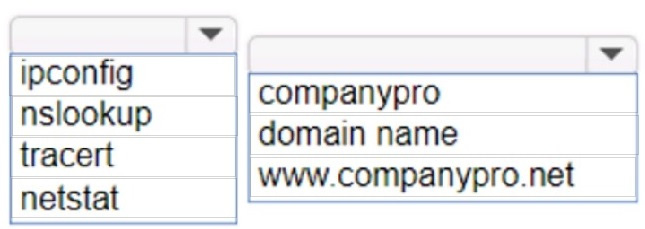
HOTSPOT
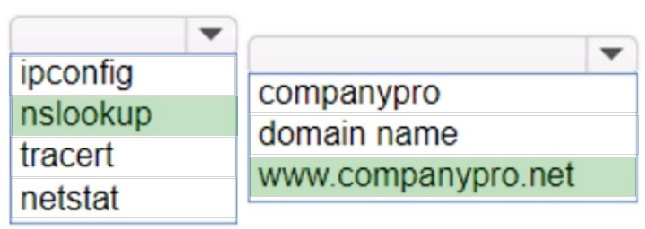
You want to list the IPv4 addresses associated with the host name www.companypro.net.
Complete the command by selecting the correct option from each drop-down list.
Hot Area: