SCS-C01 Online Practice Questions and Answers
A Developer signed in to a new account within an AWS Organizations organizations unit (OU) containing multiple accounts. Access to the Amazon S3 service is restricted with the following SCP:
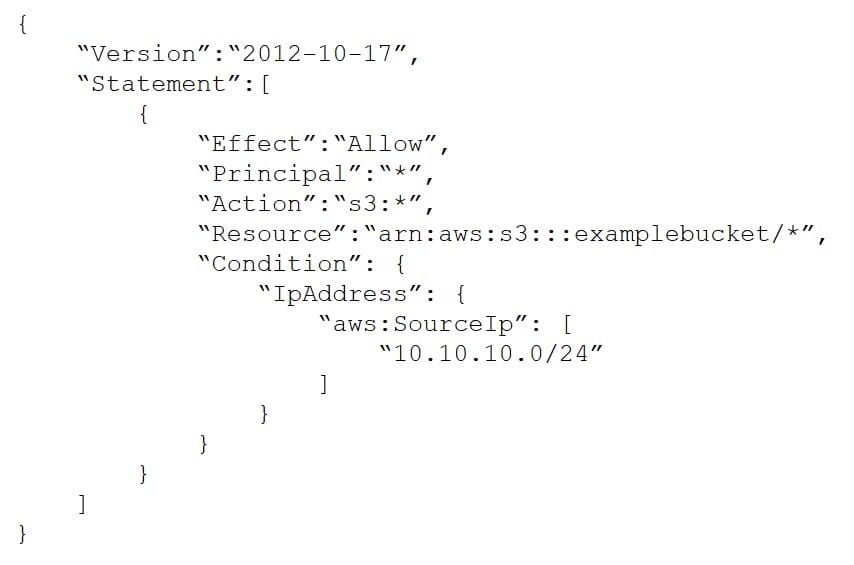
How can the Security Engineer provide the Developer with Amazon S3 access without affecting other accounts?
A. Move the SCP to the root OU of Organizations to remove the restriction to access Amazon S3.
B. Add an IAM policy for the Developer, which grants S3 access.
C. Create a new OU without applying the SCP restricting S3 access. Move the Developer account to this new OU.
D. Add an allow list for the Developer account for the S3 service.
Your development team has started using AWS resources for development purposes. The AWS account has just been created. Your IT Security team is worried about possible leakage of AWS keys. What is the first level of measure that should be taken to protect the AWS account.
Please select:
A. Delete the AWS keys for the root account
B. Create IAM Groups
C. Create IAM Roles
D. Restrict access using IAM policies
An ecommerce website was down for 1 hour following a DDoS attack. Users were unable to connect to the website during the attack period. The ecommerce company's security team is worried about future potential attacks and wants to prepare for such events. The company needs to minimize downtime in its response to similar attacks in the future.
Which steps would help achieve this? (Choose two.)
A. Enable Amazon GuardDuty to automatically monitor for malicious activity and block unauthorized access.
B. Subscribe to AWS Shield Advanced and reach out to AWS Support in the event of an attack.
C. Use VPC Flow Logs to monitor network: traffic and an AWS Lambda function to automatically block an attacker's IP using security groups.
D. Set up an Amazon CloudWatch Events rule to monitor the AWS CloudTrail events in real time use AWS Config rules to audit the configuration, and use AWS Systems Manager for remediation.
E. Use AWS WAF to create rules to respond to such attacks
You company has mandated that all data in AWS be encrypted at rest. How can you achieve this for EBS volumes? Choose 2 answers from the options given below
Please select:
A. Use Windows bit locker for EBS volumes on Windows instances
B. Use TrueEncrypt for EBS volumes on Linux instances
C. Use AWS Systems Manager to encrypt the existing EBS volumes
D. Boot EBS volume can be encrypted during launch without using custom AMI
You are building a large-scale confidential documentation web server on AWSand all of the documentation for it will be stored on S3. One of the requirements is that it cannot be publicly accessible from S3 directly, and you will need to use Cloud Front to accomplish this. Which of the methods listed below would satisfy the requirements as outlined? Choose an answer from the options below
Please select:
A. Create an Identity and Access Management (IAM) user for CloudFront and grant access to the objects in your S3 bucket to that IAM User.
B. Create an Origin Access Identity (OAI) for CloudFront and grant access to the objects in your S3 bucket to that OAl.
C. Create individual policies for each bucket the documents are stored in and in that policy grant access to only CloudFront.
D. Create an S3 bucket policy that lists the CloudFront distribution ID as the Principal and the target bucket as the Amazon Resource Name (ARN).
A company is using Amazon GuardDuty in its AWS environment. The company asks a security engineer to suspend GuardDuty. Which combination of steps must the security engineer perform to meet this requirement? (Choose two.)
A. Disable all optional data sources from all detectors in all regions.
B. Disassociate or delete all member accounts.
C. Disable all associated monitoring services.
D. Delete all existing findings.
E. Export all existing findings.
A security administrator is setting up a new AWS account. The security administrator wants to secure the data that a company stores in an Amazon S3 bucket. The security administrator also wants to reduce the chance of unintended data exposure and the potential for misconfiguration of objects that are in the S3 bucket.
Which solution will meet these requirements with the LEAST operational overhead?
A. Configure the S3 Block Public Access feature for the AWS account.
B. Configure the S3 Block Public Access feature for all objects that are in the bucket.
C. Deactivate ACLs for objects that are in the bucket.
D. Use AWS PrivateLink for Amazon S3 to access the bucket.
A company's policies require that code be validated to ensure that the code has not been altered before invocation. A security engineer needs to update code in an AWS Lambda function. The developer has finalized the code and has stored the code in an Amazon S3 bucket.
Which combination of steps should the security engineer take to meet these requirements? (Choose two.)
A. Deploy the new code in a zip file to the S3 bucket.
B. Invoke a signing job by using AWS Signer. Deploy the new signed code to the Lambda function.
C. Use AWS Key Management Service (AWS KMS) to encrypt the code.
D. Analyze the code with Amazon CodeGuru.
E. Store all passwords in AWS Secrets Manager.
A company is using Amazon Elastic Container Service (Amazon ECS) to run its container-based application on AWS. The company needs to ensure that the container images contain no severe vulnerabilities. The company also must ensure that only specific IAM roles and specific AWS accounts can access the container images.
Which solution will meet these requirements with the LEAST management overhead?
A. Pull images from the public container registry. Publish the images to Amazon Elastic Container Registry (Amazon ECR) repositories with scan on push configured in a centralized AWS account. Use a CI/CD pipeline to deploy the images to different AWS accounts. Use identity-based policies to restrict access to which IAM principals can access the images.
B. Pull images from the public container registry. Publish the images to a private container registry that is hosted on Amazon EC2 instances in a centralized AWS account. Deploy host-based container scanning tools to EC2 instances that run Amazon ECS. Restrict access to the container images by using basic authentication over HTTPS.
C. Pull images from the public container registry. Publish the images to Amazon Elastic Container Registry (Amazon ECR) repositories with scan on push configured in a centralized AWS account. Use a CI/CD pipeline to deploy the images to different AWS accounts. Use repository policies and identity-based policies to restrict access to which IAM principals and accounts can access the images.
D. Pull images from the public container registry. Publish the images to AWS CodeArtifact repositories in a centralized AWS account. Use a CI/CD pipeline to deploy the images to different AWS accounts. Use repository policies and identity-based policies to restrict access to which IAM principals and accounts can access the images.
A security team has received an alert from Amazon GuardDuty that AWS CloudTrail logging has been disabled. The security team's account has AWS Config, Amazon Inspector, Amazon Detective, and AWS Security Hub enabled. The security team wants to identify who disabled CloudTrail and what actions were performed while CloudTrail was disabled.
What should the security team do to obtain this information?
A. Use AWS Config to search for the CLOUD_TRAIL_ENABLED event. Use the configuration recorder to find all activity that occurred when CloudTrail was disabled.
B. Use Amazon Inspector to find the details of the CloudTrailLoggingDisabled event from GuardDuly, including the user name and all activity that occurred when CloudTrail was disabled.
C. Use Detective to find the details of the CloudTrailLoggingDisabled event from GuardDuty, including the user name and all activity that occurred when CloudTrail was disabled.
D. Use GuardDuty to find which user generated the CloudTrailLoggingDisabled event. Use Security Hub to find the trace of activity related to the event.


