98-367 Online Practice Questions and Answers
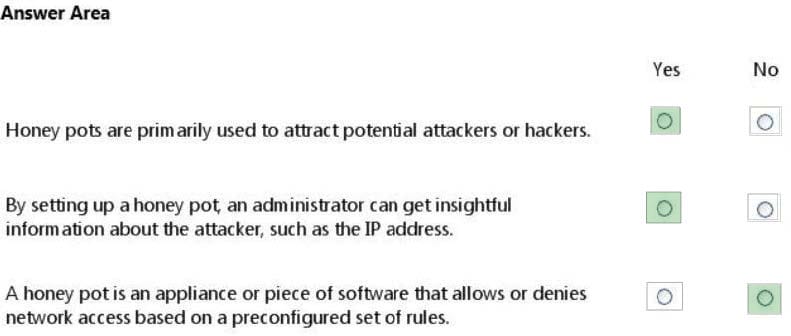
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:
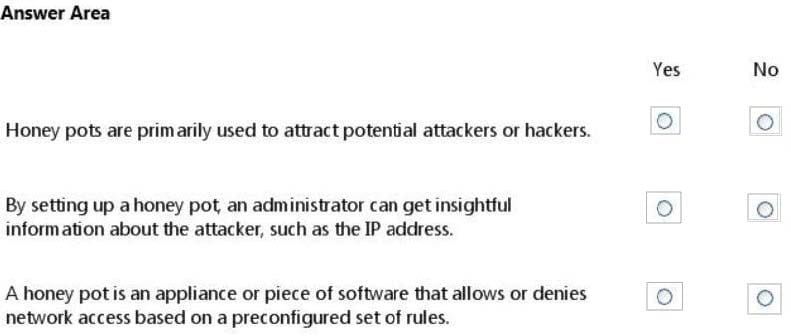
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Hot Area:

You are volunteering at an organization that gets a brand new web server. To make the server more secure, you should add a second administrator account.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text makes the statement correct.
A. Disable unused services
B. Enable LM authentication
C. Enable NTLM authentication
D. No change is needed.
The primary method of authentication in an SSL connection is passwords.
To answer, choose the option "No change is needed" if the underlined text is correct. If the underlined text is not correct, choose the correct answer.
A. No change is needed
B. Certificates
C. IPsec
D. Biometrics
E-mail bombing attacks a specific entity by:
A. Redirecting all e-mail to another entity
B. Sending high volumes of e-mail
C. Tracing e-mail to the destination address
D. Triggering high levels of security alerts
You have an application that uses IPsec to secure communications between an Internet client and a server on the internal network.
To which network security service must the IPsec client connect?
A. SFTP
B. SSH
C. VPN
D. RADIUS
Mark works as a Network Administrator fot Blue Well Inc. The company has a Windows-based network. Mark is facing a series of problems with email spam and identifying theft via phishing scams. He wants to implement the various security measures and to provide some education because it is related to the best practices while using email. Which of the following will Mark ask to employees of his company to do when they receive an email from a company they know with a request to click the link to "verify their account information"?
A. Provide the required information
B. Hide the email
C. Use Read-only Domain Controller
D. Delete the email
Which of the following can be installed and configured to prevent suspicious emails from entering the user's network?
A. Kerberos
B. Single sign-on (SSO)
C. TCP/IP protocol
D. Microsoft Forefront and Threat Management Gateway
Which of the following ports is used by the IMAP4 protocol?
A. 443
B. 53
C. 143
D. 110
Your Web server crashes at exactly the point where it reaches 1 million total visits. You discover the cause of the server crash is malicious code. Which description best fits this code?
A. Virus
B. Worm
C. Polymorphic Virus
D. Logic Bomb