312-50 Online Practice Questions and Answers
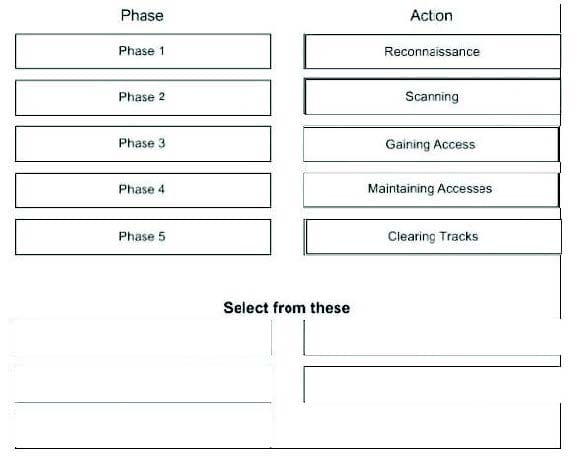
A Successfully Attack by a malicious hacker can divide into five phases, Match the order:
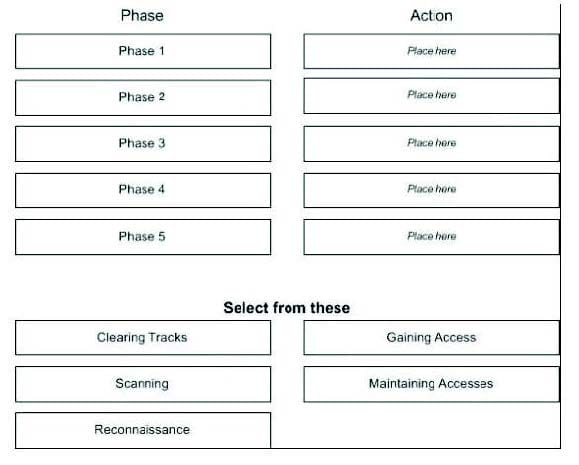
Select and Place:

How do you defend against Privilege Escalation?
A. Use encryption to protect sensitive data
B. Restrict the interactive logon privileges
C. Run services as unprivileged accounts
D. Allow security settings of IE to zero or Low
E. Run users and applications on the least privileges
What type of encryption does WPA2 use?
A. DES 64 bit
B. AES-CCMP 128 bit
C. MD5 48 bit
D. SHA 160 bit
There is some dispute between two network administrators at your company. Your boss asks you to come and meet with the administrators to set the record straight. Which of these are true about PKI and encryption? Select the best answers.
A. PKI provides data with encryption, compression, and restorability.
B. Public-key encryption was invented in 1976 by Whitfield Diffie and Martin Hellman.
C. When it comes to eCommerce, as long as you have authenticity, and authenticity, you do not need encryption.
D. RSA is a type of encryption.
While examining a log report you find out that an intrusion has been attempted by a machine whose IP address is displayed as 0xde.0xad.0xbe.0xef. It looks to you like a hexadecimal number. You perform a ping 0xde.0xad.0xbe.0xef. Which of the following IP addresses will respond to the ping and hence will likely be responsible for the the intrusion ?
A. 192.10.25.9
B. 10.0.3.4
C. 203.20.4.5
D. 222.273.290.239
E. 222.173.290.239
Bank of Timbuktu was a medium-sized, regional financial institution in Timbuktu. The bank has deployed a new Internet-accessible Web application recently, using which customers could access their account balances, transfer money between accounts, pay bills and conduct online financial business using a Web browser.
John Stevens was in charge of information security at Bank of Timbuktu. After one month in production, several customers complained about the Internet enabled banking application. Strangely, the account balances of many bank's customers has been changed! However, money hadn't been removed from the bank. Instead, money was transferred between accounts. Given this attack profile, John Stevens reviewed the Web application's logs and found the following entries:
Attempted login of unknown user: John Attempted login of unknown user: sysaR Attempted login of unknown user: sencat Attempted login of unknown user: pete `'; Attempted login of unknown user: ` or 1=1-Attempted login of unknown user: `; drop table logins-- Login of user jason, sessionID= 0x75627578626F6F6B Login of user daniel, sessionID= 0x98627579539E13BE Login of user rebecca, sessionID= 0x90627579944CCB811 Login of user mike, sessionID= 0x9062757935FB5C64 Transfer Funds user jason Pay Bill user mike Logout of user mike
What kind of attack did the Hacker attempt to carry out at the bank? (Choose the best answer)
A. The Hacker attempted SQL Injection technique to gain access to a valid bank login ID.
B. The Hacker attempted Session hijacking, in which the Hacker opened an account with the bank, then logged in to receive a session ID, guessed the next ID and took over Jason's session.
C. The Hacker attempted a brute force attack to guess login ID and password using password cracking tools.
D. The Hacker used a random generator module to pass results to the Web server and exploited Web application CGI vulnerability.
Annie has just succeeded is stealing a secure cookie via a XSS attack. She is able to replay the cookie even while the session is valid on the server. Why do you think this is possible?
A. Any Cookie can be replayed irrespective of the session status
B. The scenario is invalid as a secure cookie can't be replayed
C. It works because encryption is performed at the network layer (layer 1 encryption)
D. It works because encryption is performed at the application layer (Single Encryption Key)
The SYN Flood attack sends TCP connections requests faster than a machine can process them.
Attacker creates a random source address for each packet. SYN flag set in each packet is a request to open a new connection to the server from the spoofed IP Address Victim responds to spoofed IP Address then waits for confirmation that never arrives (timeout wait is about 3 minutes) Victim's connection table fills up waiting for replies and ignores new connection legitimate users are ignored and will not be able to access the server
How do you protect your network against SYN Flood attacks?
A. SYN cookies. Instead of allocating a record, send a SYN-ACK with a carefully constructed sequence number generated as a hash of the clients IP Address port number and other information. When the client responds with a normal ACK, that special sequence number will be included, which the server then verifies. Thus the server first allocates memory on the third packet of the handshake, not the first.
B. RST cookies The server sends a wrong SYN|ACK back to the client. The client should then generate a RST packet telling the server that something is wrong. At this point, the server knows the client is valid and will now accept incoming connections from that client normally.
C. Micro Blocks. Instead of allocating a complete connection, simply allocate a micro-record of 16- bytes for the incoming SYN object.
D. Stack Tweaking. TCP can be tweaked in order to reduce the effect of SYN floods. Reduce the timeout before a stack frees up the memory allocated for a connection.
A zone file consists of which of the following Resource Records (RRs)?
A. DNS, NS, AXFR, and MX records
B. DNS, NS, PTR, and MX records
C. SOA, NS, AXFR, and MX records
D. SOA, NS, A, and MX records
Which of the following is an automated vulnerability assessment tool.
A. Whack a Mole
B. Nmap
C. Nessus
D. Kismet
E. Jill32