2V0-651 Online Practice Questions and Answers
An administrator has installed a View security server and needs to verify that the installation was successful.
In addition to the security server, which three services should be installed? (Choose three.)
A. VMware View Framework
B. VMware View Security Framework
C. VMware View PCoIP Secure Gateway
D. VMware View Security Gateway
E. VMware View Framework Gateway
An administrator is deleting a manual pool that contains unmanaged desktop sources and selects the Leave active option.
How will the administrator's action affect connections to the pool?
A. Connections will remain active until the user logs off.
B. Connections will be accepted until the desktop source is unregistered.
C. Connections will remain active for the period of time specified by the administrator.
D. Connections will remain available until the next session state monitoring interval.
An administrator is configuring a Group Policy Object (GPO) for an Organizational Unit (OU) that contains virtual Windows 7 desktops. The administrator needs several user settings to apply only to users accessing desktops in this OU.
After configuring the GPO, the administrator notices that the group policy user settings are not being applied.
Why are the user settings not being applied?
A. The Loopback processing GPO setting was not enabled on the Computers OU.
B. The OU does not contain both User and Computer objects.
C. The Windows 7 desktops were not restarted after GPO was configured.
D. The user settings must also be applied to the default Users OU.
An administrator is running a View Infrastructure with Linked Clones running on ESXi 5.x. Users should not be able to eject devices such as CD-ROMs from the virtual desktops.
What should the administrator do on the vSphere Client to prevent users from ejecting devices?
A. Right click on the parent image, and then in Edit Settings-->Options, disable Hot Add.
B. Modify the parent image .vmx file, and set devices.hotplug to False.
C. Modify the parent image .nvram file, and set devices.hotplug to False.
D. Right click on the parent image and then in Edit Settings-->Hardware, disable Hot Plug.
What must the administrator do next to fulfill the stated requirements?
An administrator has built a Centralized Virtual Desktop (CVD) using the Mirage default CVD policy, but finds that the D. drive on all users' machines are not centralized correctly.
Which changes should the administrator make to include the additional volume?
A. Create a new Upload policy that includes the D. drive in backup and restore.
B. Add a Protected Volume in the Upload policy.
C. Modify the CVD to include all system drives.
D. Add %ANYVOLUME% to the User Area of the Upload policy.
An administrator is planning the capture of a reference machine for two departments: Finance and Information Technology.
Which two applications should the administrator include in the common base layer? (Choose two.)
A. Finance Accounting Application
B. Anti-Virus software
C. Admin Script Editor
D. VPN Software
Several users within a corporation installed a team collaboration utility onto their Mirage- managed systems. The systems became erratic, so they uninstalled the application, but the problem remained.
An administrator needs to repair the users' systems and ensure they are compliant with the corporate image. All user profile data must remain intact.
What should the administrator do?
A. Revert to Snapshot with Restore System Only option selected.
B. Enforce All Layers with the Preserve user applications option selected.
C. Revert to Snapshot without Restore System Only option selected.
D. Enforce All Layers with the Remove user applications option selected.
After creating an Upload policy for a group of users, an administrator has found a significant increase in storage usage by Mirage. After further investigation, the administrator finds that the increase is a result of users storing personal MP3 libraries on the system.
What should the administrator do to prevent these files from being protected while allowing the users to store the files on the system?
A. Add a Rule to the User Area for MP3 files in the Upload policy.
B. Create a Collection labeled Exclude MP3s.
C. Add a Rule Exception to the Unprotected Area for MP3 files in the Upload policy.
D. Add a Rule to the Unprotected Area for MP3 files in the Upload policy.
Refer to the Exhibit.
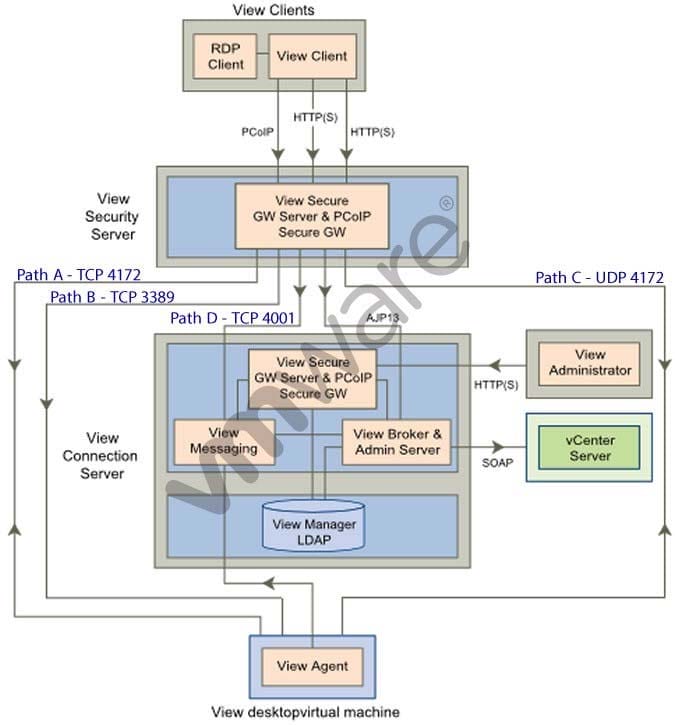
Based on the exhibit, which pathway is used for RDP traffic?
A. Path A
B. Path B
C. Path C
D. Path D
Refer to the Exhibit.

Based on the exhibit, which two paths are used for PCoIP traffic? (Choose two.)
A. Path A
B. Path B
C. Path C
D. Path D

