250-315 Online Practice Questions and Answers
Which task should an administrator perform to troubleshoot operation of the Symantec Endpoint Protection embedded database?
A. verify that dbsrv11.exe is listening on port 2638
B. check whether the MSSQLSERVER service is running
C. verify the sqlserver.exe service is running on port 1433
D. check the database transaction logs in X:\Program Files\Microsoft SQL server
An administrator is unable to delete a location. What is the likely cause?
A. The location currently contains clients.
B. Criteria is defined within the location.
C. The administrator has client control enabled.
D. The location is currently assigned as the default location.
A company plans to install six Symantec Endpoint Protection Managers (SEPMs) spread evenly across two sites. The administrator needs to direct replication activity to SEPM3 server in Site 1 and SEPM4 in Site 2.
Which two actions should the administrator take to direct replication activity to SEPM3 and SEPM4? (Select two.)
A. Install SEPM3 and SEPM4 after the other SEPMs
B. Install the SQL Server databases on SEPM3 and SEPM4
C. Ensure SEPM3 and SEPM4 are defined as the top priority server in the Site Settings
D. Ensure SEPM3 and SEPM4 are defined as remote servers in the replication partner configuration
E. Install IT Analytics on SEPM3 and SEPM4
A company needs to forward log data from Data Center A to Data Center B during off peak hours only. How should the company architect its Symantec Endpoint Protection environment?
A. Set up two sites and schedule replication between them during off peak hours
B. Set up a single site and configure the clients to send their logs to the Manager during off peak hours
C. Set up a Group Update Provider (GUP) at Data Center A and configure it to send logs during off peak hours
D. Set up a LiveUpdate Server at Data Center A and configure it to send logs during off peak hours
What are two supported Symantec Endpoint Protection Manager authentication types? (Select two.)
A. Microsoft Active Directory
B. MS-CHAP
C. RSA SecurID
D. Biometrics
E. Network Access Control
A Symantec Endpoint Protection (SEP) administrator is remotely deploying SEP clients, but the clients are failing to install on Windows XP.
What are two possible reasons for preventing installation? (Select two.)
A. Windows firewall is enabled.
B. Internet Connection firewall is disabled.
C. Administrative file shares are enabled.
D. Simple file sharing is enabled.
E. Clients are configured for DHCP.
Refer to the exhibit.
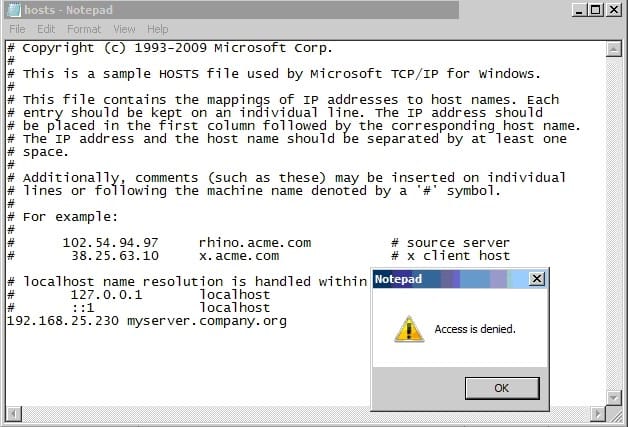
In the use case displayed in the exhibit, why is Notepad unable to save the changes to this file?
A. Tamper Protection is preventing Notepad from modifying the host file.
B. SONAR is set to block host file modifications.
C. System Lockdown is enabled.
D. SONAR High Risk detection is set to Block.
Which protection engine should be enabled to drop malicious vulnerability scans against a client system?
A. SONAR
B. Intrusion Prevention
C. Tamper Protection
D. Application and Device Control
Refer to the exhibit.
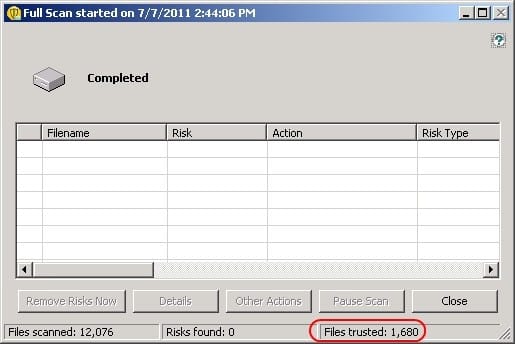
Which settings can impact the Files trusted count?
A. SONAR settings in the Virus and Spyware Protection policy
B. System Lockdown Whitelist in the Application and Device Control policy
C. Insight settings in the Virus and Spyware Protection policy
D. File Cache settings in the Virus and Spyware Protection policy
Refer to the exhibit.
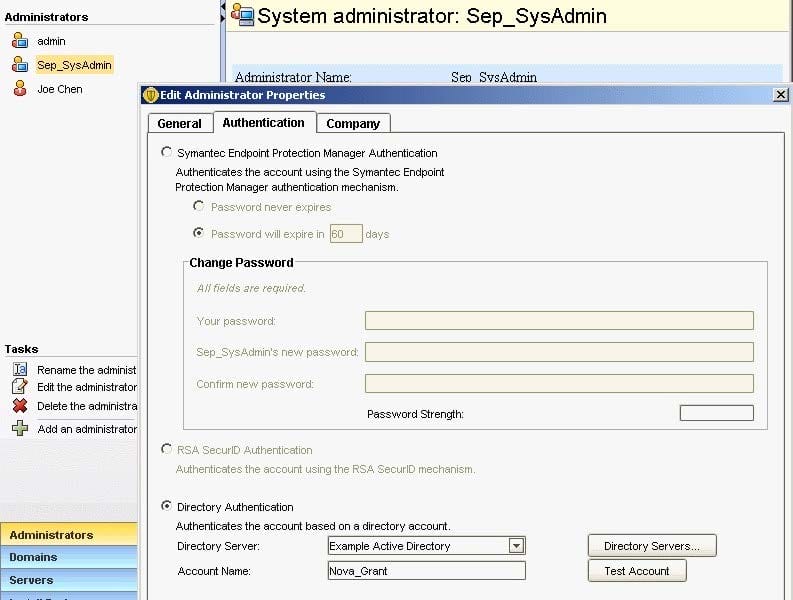
An administrator has configured the Symantec Endpoint Protection Manager (SEPM) to use Active Directory authentication. The administrator defines a new Symantec Endpoint Protection administrator named Sep_SysAdmin, configured to use Directory Authentication.
Which password needs to be entered when the administrator logs in to the SEPM console as Sep_SysAdmin?
A. The password for the Active Directory account Nova_Grant
B. The password for the SEPM account Nova_Grant
C. The password for the Active Directory account Sep_SysAdmin
D. The password for the SEPM account Sep_SysAdmin

