200-201 Online Practice Questions and Answers
Refer to the exhibit.

Which technology generates this log?
A. NetFlow
B. IDS
C. web proxy
D. firewall
An organization is cooperating with several third-party companies. Data exchange is on an unsecured channel using port 80 Internal employees use the FTP service to upload and download sensitive data An engineer must ensure confidentiality while preserving the integrity of the communication. Which technology must the engineer implement in this scenario'?
A. X 509 certificates
B. RADIUS server
C. CA server
D. web application firewall
Refer to the exhibit.

Which type of attack is being executed?
A. SQL injection
B. cross-site scripting
C. cross-site request forgery
D. command injection
Why is HTTPS traffic difficult to screen?
A. HTTPS is used internally and screening traffic (or external parties is hard due to isolation.
B. The communication is encrypted and the data in transit is secured.
C. Digital certificates secure the session, and the data is sent at random intervals.
D. Traffic is tunneled to a specific destination and is inaccessible to others except for the receiver.
What is the difference between vulnerability and risk?
A. A vulnerability is a sum of possible malicious entry points, and a risk represents the possibility of the unauthorized entry itself.
B. A risk is a potential threat that an exploit applies to, and a vulnerability represents the threat itself
C. A vulnerability represents a flaw in a security that can be exploited, and the risk is the potential damage it might cause.
D. A risk is potential threat that adversaries use to infiltrate the network, and a vulnerability is an exploit
How does statistical detection differ from rule-based detection?
A. Statistical detection involves the evaluation of events, and rule-based detection requires an evaluated set of events to function.
B. Statistical detection defines legitimate data over time, and rule-based detection works on a predefined set of rules
C. Rule-based detection involves the evaluation of events, and statistical detection requires an evaluated set of events to function Rule-based detection defines
D. legitimate data over a period of time, and statistical detection works on a predefined set of rules
A network engineer noticed in the NetFlow report that internal hosts are sending many DNS requests to external DNS servers. A SOC analyst checked the endpoints and discovered that they are infected and became part of the botnet. Endpoints are sending multiple DNS requests, but with spoofed IP addresses of valid external sources. What kind of attack are infected endpoints involved in?
A. DNS tunneling
B. DNS hijacking
C. DNS amplification
D. DNS flooding
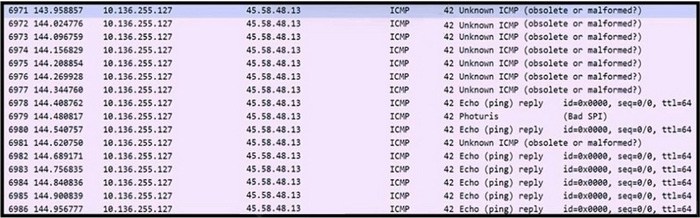
Refer to the exhibit. An engineer received a ticket to analyze unusual network traffic. What is occurring?
A. data exfiltration
B. regular network traffic; no suspicious activity
C. denial-of-service attack
D. cookie poisoning
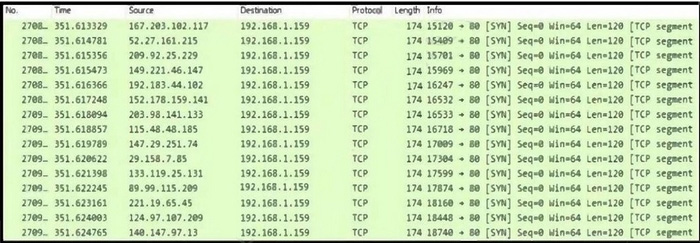
Refer to exhibit. An engineer is investigating an intrusion and is analyzing the pcap file. Which two key elements must an engineer consider? (Choose two.)
A. variable "info" field and unchanging sequence number
B. high volume of SYN packets with very little variance in time
C. SYN packets acknowledged from several source IP addresses
D. identical length of 120 and window size (64)
E. same source IP address with a destination port 80
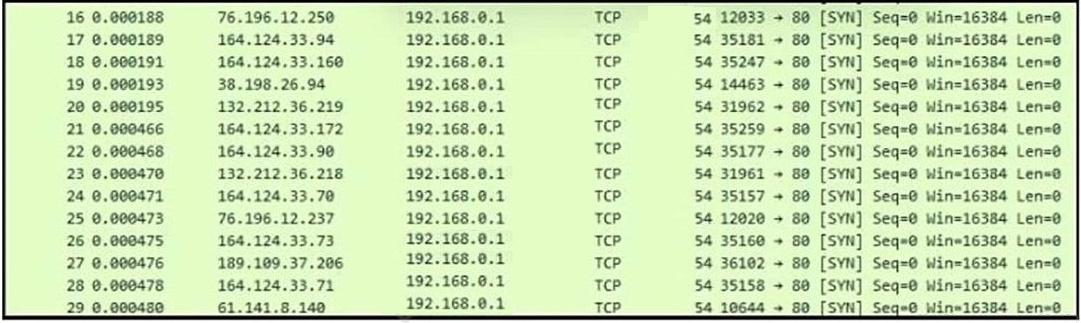
Refer to the exhibit. What is occurring?
A. ARP spoofing attack
B. man-in-the-middle attack
C. brute-force attack
D. denial-of-service attack

