1Y0-440 Online Practice Questions and Answers
A Citrix Architect can execute a configuration job using a DeployMasterConfiguration template on a NetScaler_________deployed_________. (Choose the correct option to complete sentence.)
A. CPX; as part of a high availability pair
B. CPX; as a stand alone device
C. SDX; with less than 6 partitions and dedicated management interface
D. MPX; as part of the cluster but Cluster IP is NOT configured
E. SDX; with no partitions as a stand alone device
Scenario: A Citrix Architect holds a design discussion with a team of Workspacelab members, and they capture the following requirements for the NetScaler design project.
1.
A pair of NetScaler MPX appliances will be deployed in the DMZ network and another pair in the internal network.
2.
High availability will be accessible between the pair of NetScaler MPX appliances in the DMZ network.
3.
Multi-factor authentication must be configured for the NetScaler Gateway virtual server.
4.
The NetScaler Gateway virtual server is integrated with the StoreFront server.
5.
Load balancing must be deployed for users from the workspacelab.com domain.
6.
The workspacelab users should be authenticated using Cert Policy and LDAP.
7.
All the client certificates must be SHA 256-signed, 2048 bits, and have UserPrincipalName as the subject.
8.
Single Sign-on must be performed between StoreFront and NetScaler Gateway.
After deployment, the architect observes that LDAP authentication is failing.
Click the Exhibit button to review the output of aaad debug and the configuration of the authentication policy.
Exhibit 1
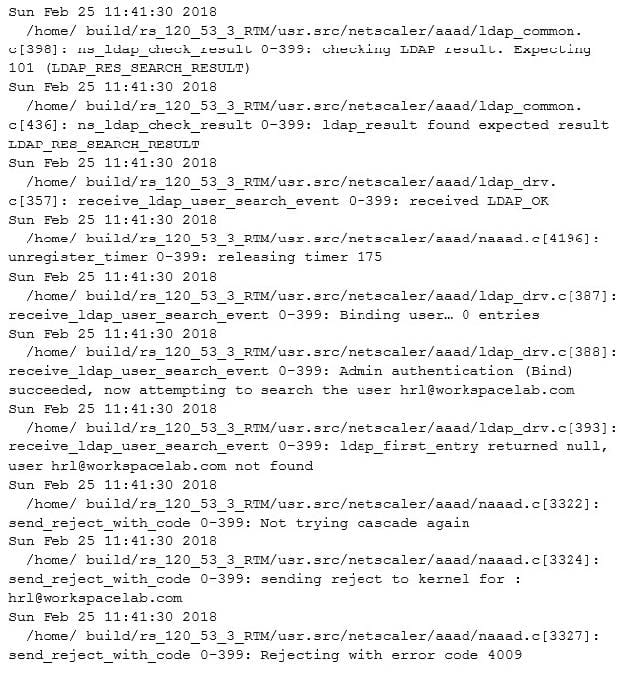
Exhibit 2
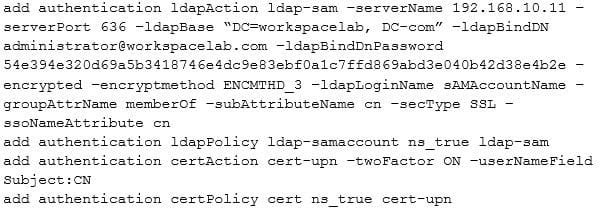
What is causing this issue?
A. UserNamefield is set as subjection
B. Password used is incorrect
C. User does NOT exist in database
D. IdapLoginName is set as sAMAccountName
Which markup language can a Citrix use along with NITRO API to create a StyleBook?
A. GML
B. XML
C. HTML
D. YAML
Scenario: The Workspacelab team has configured their NetScaler Management and Analytics (NMAS) environment. A Citrix Architect needs to log on to the NMAS to check the settings.
Which two authentication methods are supported to meet this requirement? (Choose two.)
A. Certificate
B. RADIUS
C. TACACS
D. Director
E. SAML
F. AAA
Scenario: A Citrix Architect has configured NetScaler Gateway integration with a XenApp environment to provide access to users from two domains: vendorlab.com and workslab.com. The Authentication method used is LDAP.
Which two steps are required to achieve Single Sign-on StoreFront using a single store? (Choose two.)
A. Configure Single sign-on domain in Session profile `userPrincipalName'.
B. Do NOT configure SSO Name attribute in LDAP Profile.
C. Do NOT configure sign-on domain in Session Profile.
D. Configure SSO Name attribute to `userPrincipalName' in LDAP Profile.
Scenario: A Citrix Architect needs to assess a NetScaler Gateway deployment that was recently completed by a customer and is currently in pre-production testing. The NetScaler Gateway needs to use ICA proxy to provide access to a XenApp and XenDesktop environment. During the assessment, the customer informs the architect that users are NOT able to launch published resources using the Gateway virtual server.
Click the Exhibit button to view the troubleshooting details collected by the customer.

What is the cause of this issue?
A. The required ports have NOT been opened on the firewall between the NetScaler gateway and the Virtual Delivery Agent (VDA) machines.
B. The StoreFront URL configured in the NetScaler gateway session profile is incorrect.
C. The Citrix License Server is NOT reachable.
D. The Secure Ticket Authority (STA) servers are load balanced on the NetScaler.
Scenario: A Citrix Architect needs to design a hybrid XenApp and XenDesktop environment which will include Citrix Cloud as well as resource locations in an on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
1.
Active XenApp and XenDesktop Service subscription
2.
No existing NetScaler deployment
3.
Global Server Load Balancing is used to direct connection requests to Location B, if the StoreFront server in Location B fails, connections should be directed to Location A.
Click the Exhibit button to view the conceptual environment architecture.
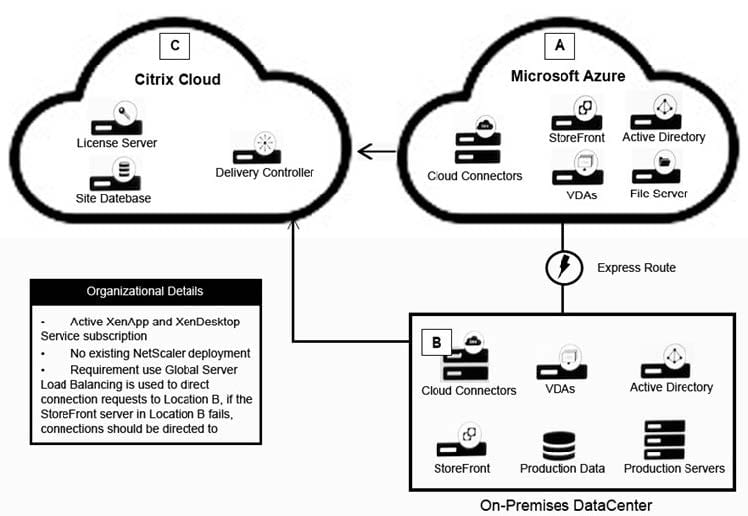
The architect should use _____ in Location A, and should use ________ in Location B. (Choose the correct option to complete the sentence.)
A. NetScaler ADC (BYO); NetScaler gateway appliance
B. NetScaler ADC (BYO); No NetScaler products
C. NetScaler ADC (BYO); NetScaler ADC (BYO)
D. NetScaler Gateway appliance; NetScaler Gateway appliance
E. NetScaler Gateway appliance; NetScaler ADC (BYO)
A Citrix Architect needs to configure advanced features of NetScaler by using StyleBooks as a resource in the Heat service.
What is the correct sequence of tasks to be completed for configuring NetScaler using the Heat stack?
A. 1. Install NetScaler Bundle for OpenStack
2.
Deploy the Heat stack
3.
Register OpenStack with NMAS
4.
Add NetScaler instances (Optional)
5.
Prepare the HOT by using the NetScaler heat resources and NetScaler Network Resource
6.
Create service packages (Add OpenStack tenants)
B. 1. Install NetScaler Bundle for OpenStack
2.
Register OpenStack with NMAS
3.
Add NetScaler instances (Optional)
4.
Create service packages (Add OpenStack tenants)
5.
Prepare the HOT by using the NetScaler heat resources and NetScaler Network Resource
6.
Deploy the Heat stack
C. 1. Install NetScaler Bundle for OpenStack
2.
Add NetScaler instances (Optional)
3.
Create service packages (Add OpenStack tenants)
4.
Prepare the HOT by using the NetScaler heat resources and NetScaler Network Resource
5.
Register OpenStack with NMAS
6.
Deploy the Heat stack
D. 1. Install NetScaler Bundle for OpenStack
2.
Prepare the HOT by using the NetScaler heat resources and NetScaler Network Resource
3.
Register OpenStack with NMAS
4.
Deploy the Heat stack
5.
Add NetScaler instances (Optional)
6.
Create service packages (Add OpenStack tenants)
Which NetScaler Management and Analytics System (NMAS) utility can a Citrix Architect utilize to verify the configuration template created by the NMAS StyleBook, before actually executing it on the NetScaler?
A. Dry Run
B. configpack
C. NITRO API
D. configcheck
Scenario: A Citrix Architect needs to configure a full VPN session profile to meet the following requirements:
1.
Users should be able to send the traffic only for the allowed networks through the VPN tunnel.
2.
Only the DNS requests ending with the configured DNS suffix workspacelab.com must be sent to NetScaler Gateway.
3.
If the DNS query does NOT contain a domain name, then DNS requests must be sent to NetScaler gateway.
Which settings will meet these requirements?
A. Split Tunnel to OFF, Split DNS Both
B. Split Tunnel to ON, Split DNS Local
C. Split Tunnel to OFF, Split DNS Remote
D. Split Tunnel to ON, Split DNS Remote

