SY0-601 Online Practice Questions and Answers
Which of the following are the MOST likely vectors for the unauthorized inclusion of vulnerable code in a software company's final software releases? (Select TWO.)
A. Unsecure protocols
B. Use of penetration-testing utilities
C. Weak passwords
D. Included third-party libraries
E. Vendors/supply chain
F. Outdated anti-malware software
A cybersecurity administrator needs to allow mobile BYOD devices to access network resources. As the devices are not enrolled to the domain and do not have policies applied to them, which of the following are best practices for authentication and infrastructure security? (Select TWO).
A. Create a new network for the mobile devices and block the communication to the internal network and servers
B. Use a captive portal for user authentication.
C. Authenticate users using OAuth for more resiliency
D. Implement SSO and allow communication to the internal network
E. Use the existing network and allow communication to the internal network and servers.
F. Use a new and updated RADIUS server to maintain the best solution
Which of the following best describes a use case for a DNS sinkhole?
A. Attackers can see a DNS sinkhole as a highly valuable resource to identify a company's domain structure.
B. A DNS sinkhole can be used to draw employees away from known-good websites to malicious ones owned by the attacker.
C. A DNS sinkhole can be used to capture traffic to known-malicious domains used by attackers.
D. A DNS sinkhole can be set up to attract potential attackers away from a company's network resources.
Which of the following should be monitored by threat intelligence researchers who search for leaked credentials?
A. Common Weakness Enumeration
B. OSINT
C. Dark web
D. Vulnerability databases
A company would like to protect credit card information that is stored in a database from being exposed and reused. However, the current POS system does not support encryption. Which of the following would be BEST suited to secure this information?
A. Masking
B. Tokenization
C. DLP
D. SSL/TLS
A user's laptop constantly disconnects from the Wi-Fi network. Once the laptop reconnects, the user can reach the internet but cannot access shared folders or other network resources. Which of the following types of attacks is the user MOST likely experiencing?
A. Bluejacking
B. Jamming
C. Rogue access point
D. Evil twin
A recently discovered zero-day exploit utilizes an unknown vulnerability in the SMB network protocol to rapidly infect computers. Once infected, computers are encrypted and held for ransom. Which of the following would BEST prevent this attack from reoccurring?
A. Configure the perimeter firewall to deny inbound external connections to SMB ports.
B. Ensure endpoint detection and response systems are alerting on suspicious SMB connections.
C. Deny unauthenticated users access to shared network folders.
D. Verify computers are set to install monthly operating system, updates automatically.
Which of the following supplies non-repudiation during a forensics investigation?
A. Dumping volatile memory contents first
B. Duplicating a drive with dd
C. Using a SHA-2 signature of a drive image
D. Logging everyone in contact with evidence
E. Encrypting sensitive data
Phishing and spear-phishing attacks have been occurring more frequently against a company's staff. Which of the following would MOST likely help mitigate this issue?
A. DNSSEC and DMARC
B. DNS query logging
C. Exact mail exchanger records in the DNS
D. The addition of DNS conditional forwarders
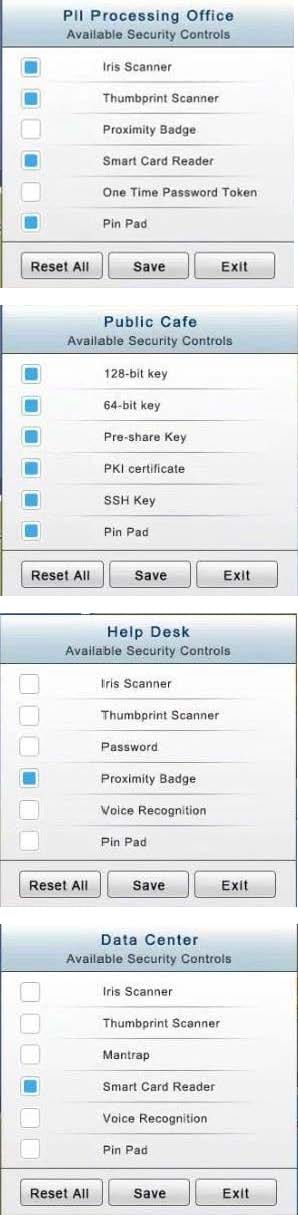
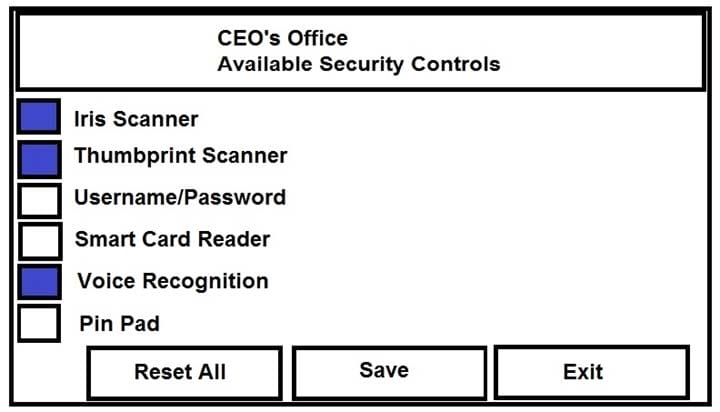
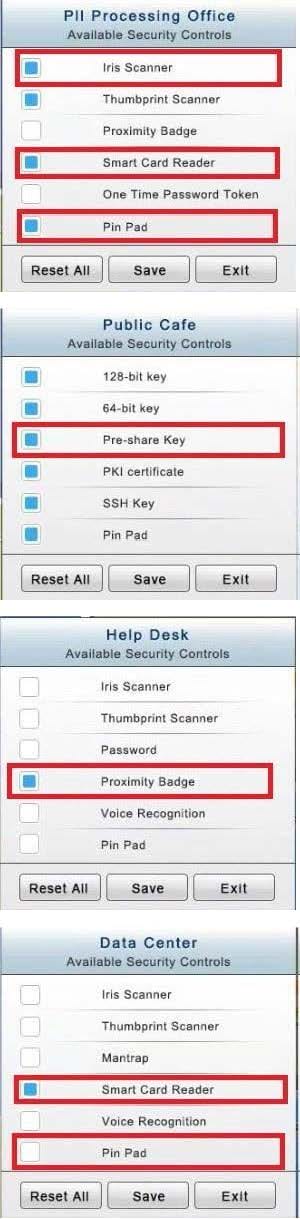
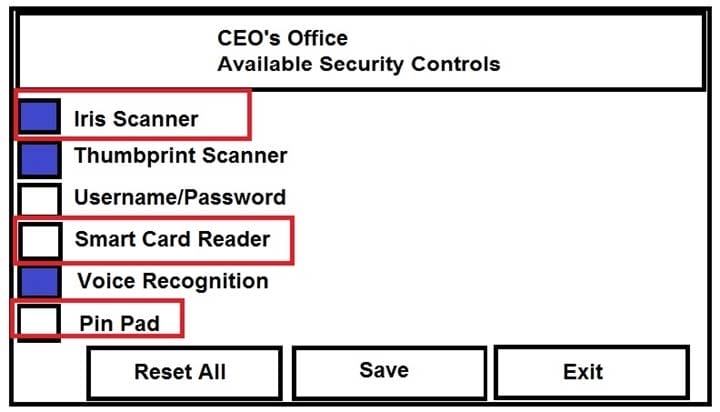
You have just received some room and WiFi access control recommendations from a security consulting company. Click on each building to bring up available security controls. Please implement the following requirements:
The Chief Executive Officer's (CEO) office had multiple redundant security measures installed on the door to the office. Remove unnecessary redundancies to deploy three-factor authentication, while retaining the expensive iris render.
The Public Cafe has wireless available to customers. You need to secure the WAP with WPA and place a passphrase on the customer receipts.
In the Data Center you need to include authentication from the "something you know" category and take advantage of the existing smartcard reader on the door.
In the Help Desk Office, you need to require single factor authentication through the use of physical tokens given to guests by the receptionist.
The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.
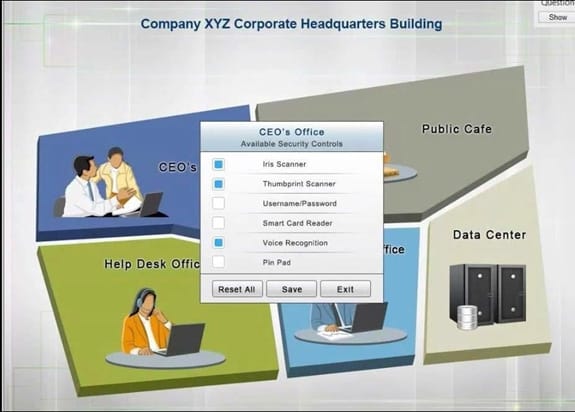
Instructions: The original security controls for each office can be reset at any time by selecting the Reset button. Once you have met the above requirements for each office, select the Save button. When you have completed the entire simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.