JN0-541 Online Practice Questions and Answers
Which statement is true about the attack object database update process?
A. Each sensor updates its own attack object database automatically; however they must be able to access the Juniper site on TCP port 443.
B. The attack object database update must be manually performed by the administrator, and the administrator must manually install it on each sensor.
C. The attack object database update can be initiated manually or automatically.
D. The attack object database update can be automatically scheduled to occur using the Security Manager GUI.
Which rule base would detect netcat?
A. SYN protector
B. traffic anomalies
C. backdoor
D. exempt
Which three columns can be seen in the Application View of the Enterprise Security Profiler? (Choose three.)
A. Service
B. Src OS Name
C. Src and Dest IPs
D. Context
E. Access Type
You implement Traffic Anomaly detection and you find numerous alerts of port scans from your security auditing team that you want to ignore. You create an address book entry for the security audit team specifying the IP addresses of those machines. What should you do next?
A. Create a rule at the top of the Traffic Anomaly rule base to ignore traffic from security audit team, and make this a terminal rule.
B. Create a rule at the top of the Traffic Anomalyrulebase to ignore traffic from security audit team.
C. Create a rule at the top of the IDPrulebase to ignore traffic from security audit team, and make this a terminal rule.
D. Create an exempt rule for the security audit team in the Exemptrulebase to ignore Traffic Anomalies.
Which interface does IDP use to communicate with Security Manager?
A. eth0
B. console port
C. eth1 D. HA port
In which three situations would you create a compound attack object? (Choose three.)
A. When the pattern "@@@@@@@@" and context "ftp-get-filename" completely define the attack.
B. When attack objects must occur in a particular order.
C. When one of the attack objects is a protocol anomaly.
D. When the pattern needs to be defined using a stream 256 context.
E. You have at least two attack objects that define a single attack.
In the Enterprise Security Profiler, what would you define under Permitted Objects?
A. Define traffic that violates your security policy.
B. Definevalid, permitted activity on the network.
C. Define any attacks that violate your security policy.
D. Define violations of permitted activity on the network.
Which three statements are true about Dynamic Groups? (Choose three.)
A. Dynamic Groups are only used inMain and Exempt rulebases.
B. A Dynamic Group can contain another static Attack Object group.
C. Objects can be added or updated to Dynamic Groups during the Signature Update process.
D. You can filter the Attack Objects based on severity, product, or direction that you want to be included in the Dynamic Group.
Which context value do you filter on to identify all webservers in a network?
A. HTTP Request Method
B. HTTP Server IP
C. HTTP Header Server
D. HTTP Header User Agent
Exhibit:
You work as an administrator at Certkiller .com. Study the exhibit carefully. In the mode shown in the exhibit, IDP Sensor can protect Server A against attacks being initiated from which three hosts? (Choose three.)
Exhibit:
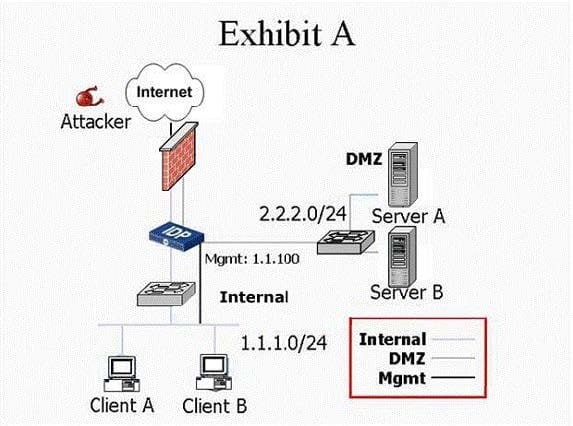
A. Attacker
B. Server B
C. Client B
D. Client A

