312-49V8 Online Practice Questions and Answers
A. Errors-To header
B. Content-Transfer-Encoding header
C. Mime-Version header
D. Content-Type header
Determine the message length from following hex viewer record: A. 6E2F
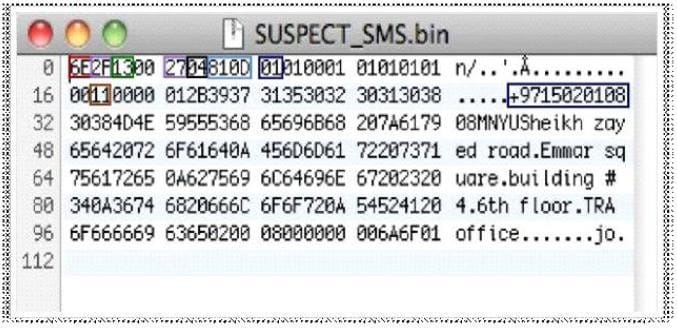
B. 13
C. 27
D. 810D
Computer security logs contain information about the events occurring within an organization's systems and networks. Application and Web server log files are useful in detecting web attacks. The source, nature, and time of the attack can be determined by _________of the compromised system.
A. Analyzing log files
B. Analyzing SAM file
C. Analyzing rainbow tables
D. Analyzing hard disk boot records
At the time of evidence transfer, both sender and receiver need to give the information about date and time of transfer in the chain of custody record.
A. True
B. False
What is the "Best Evidence Rule"?
A. It states that the court only allows the original evidence of a document, photograph, or recording at the trial rather than a copy
B. It contains system time, logged-on user(s), open files, network information, process information, process-to-port mapping, process memory, clipboard contents, service/driver information, and command history
C. It contains hidden files, slack space, swap file, index.dat files, unallocated clusters, unused partitions, hidden partitions, registry settings, and event logs
D. It contains information such as open network connection, user logout, programs that reside in memory, and cache data
Identify the attack from following sequence of actions? Step 1: A user logs in to a trusted site and creates a new session Step 2: The trusted site stores a session identifier for the session in a cookie in the web browser Step 3: The user is tricked to visit a malicious site Step 4: the malicious site sends a request from the user's browser using his session cookie
A. Web Application Denial-of-Service (DoS) Attack
B. Cross-Site Scripting (XSS) Attacks
C. Cross-Site Request Forgery (CSRF) Attack
D. Hidden Field Manipulation Attack
Smith, an employee of a reputed forensic Investigation firm, has been hired by a private organization to investigate a laptop that is suspected to be involved in hacking of organization DC server. Smith wants to find all the values typed into the Run box in the Start menu. Which of the following registry key Smith will check to find the above information?
A. UserAssist Key
B. MountedDevices key
C. RunMRU key
D. TypedURLs key
What is static executable file analysis?
A. It is a process that consists of collecting information about and from an executable file without actually launching the file under any circumstances
B. It is a process that consists of collecting information about and from an executable file by launching the file under any circumstances
C. It is a process that consists of collecting information about and from an executable file without actually launching an executable file in a controlled and monitored environment
D. It is a process that consists of collecting information about and from an executable file by launching an executable file in a controlled and monitored environment
Raw data acquisition format creates ____________of a data set or suspect drive.
A. Simple sequential flat files
B. Segmented files
C. Compressed image files
D. Segmented image files
International Mobile Equipment Identifier (IMEI) is a 15-dlgit number that indicates the manufacturer, model type, and country of approval for GSM devices. The first eight digits of an IMEI number that provide information about the model and origin of the mobile device is also known as:
A. Type Allocation Code (TAC)
B. Device Origin Code (DOC)
C. Manufacturer identification Code (MIC)
D. Integrated Circuit Code (ICC)

